F5 Public Cloud Solutions > 2. Class - PC201 - Deploying F5 Solutions to AWS with Terraform and iControl LX Extensions > 2.6. F5 Application Services 3 Extension (AS3) Source | Edit on
2.6.1. Clean config - No Partitions or Virtual Servers¶
Big-IP1 => Local Traffic => Virtual Servers. There are no Virtual Servers configured in any partition.
Big-IP2 => Local Traffic => Virtual Servers. There are no Virtual Servers configured in any partition.
2.6.2. Check AS3 is ready¶
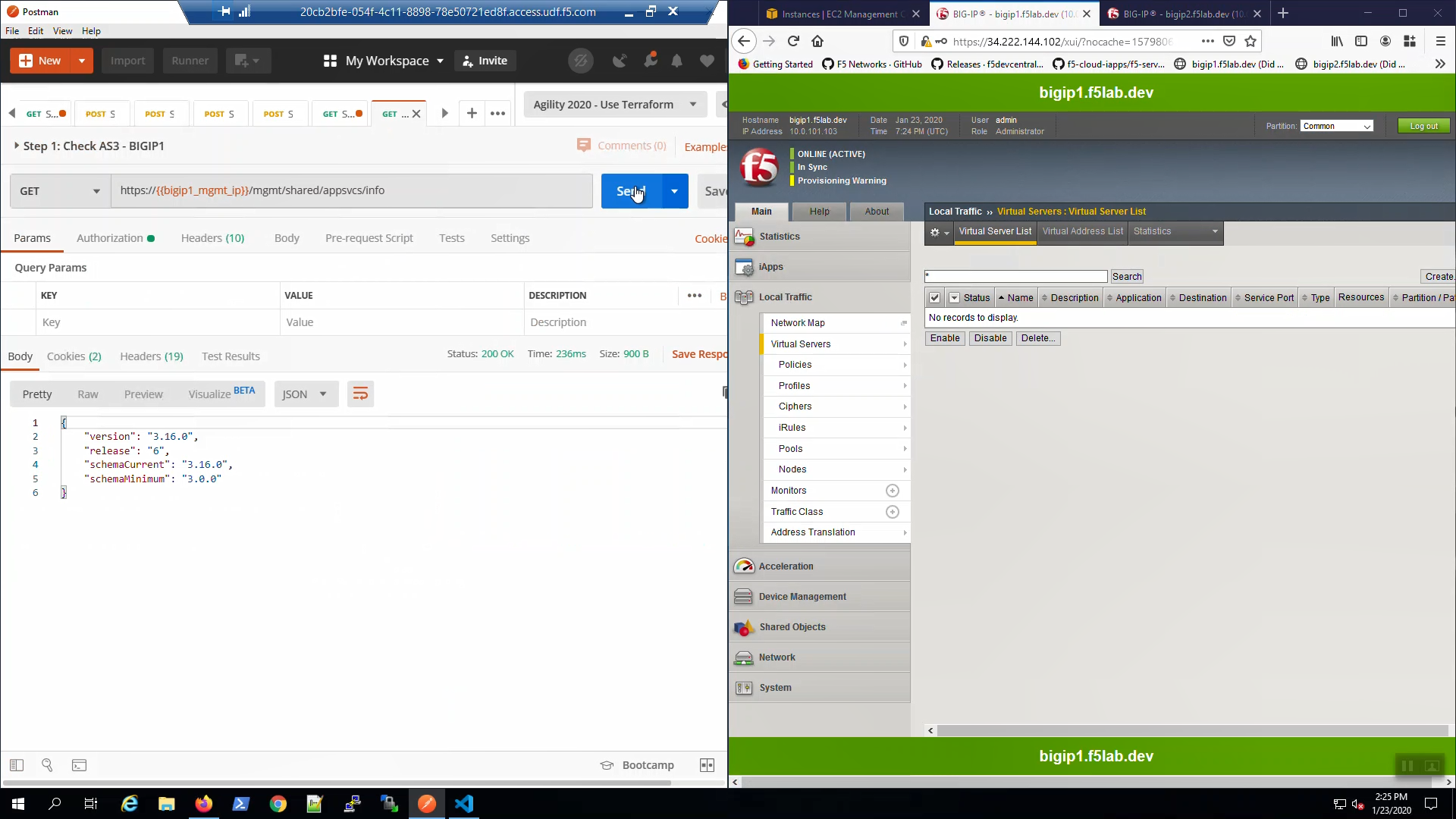
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 1: Check AS3 - BIGIP1” => [Send].
Status 200 OK response signals that Application Services 3 Extension (AS3) is ready on Big-IP1.
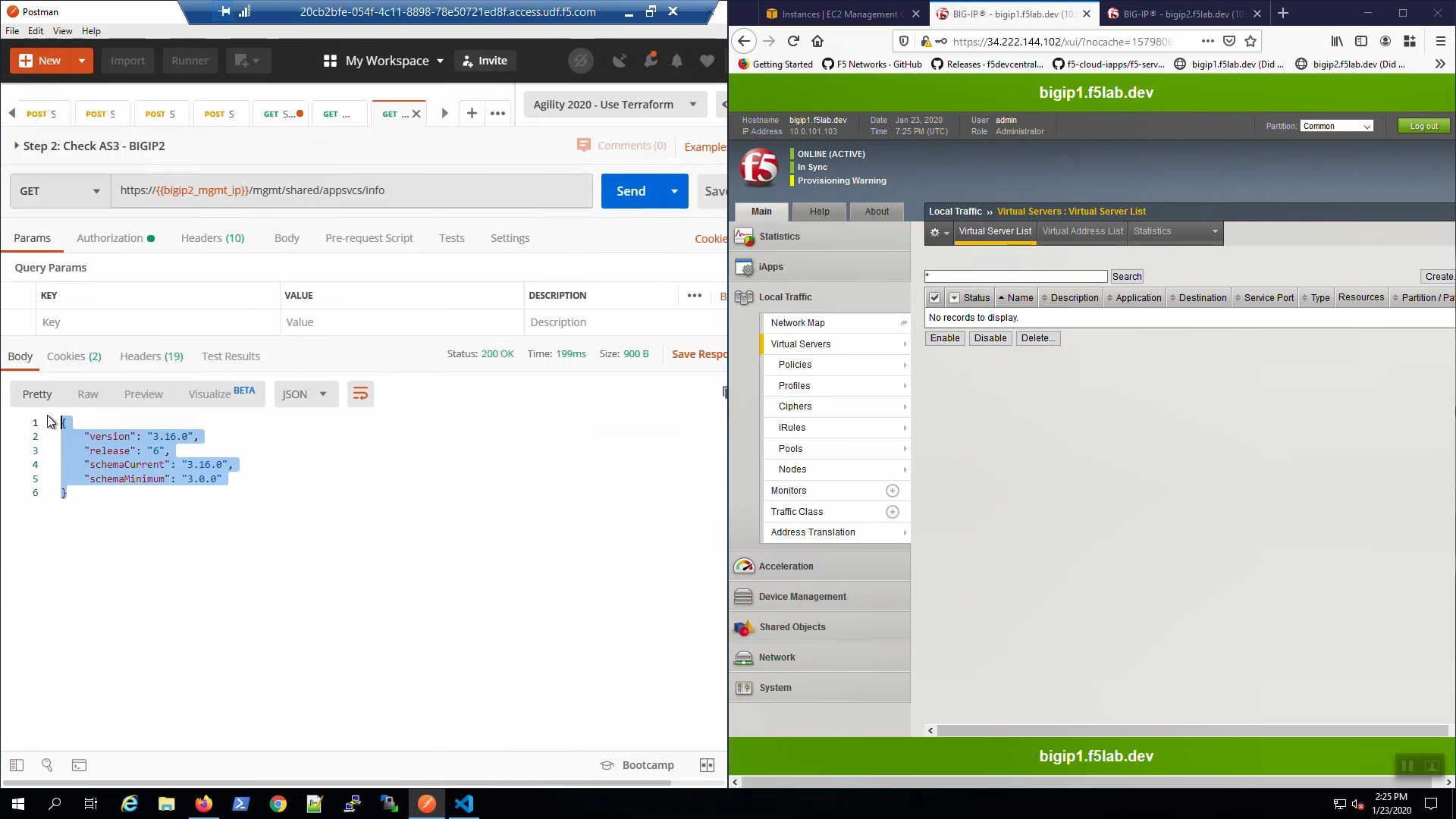
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 2: Check AS3 - BIGIP2” => [Send].
Status 200 OK response signals that Application Services 3 Extension (AS3) is ready on Big-IP2.
2.6.3. Create HTTP Virtual Servers with AS3 and Service Discovery¶
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 3: Example01/example01 with AutoDiscover pool members”. Review the Body of the declaration. The AS3 declaration is configured to discover pool members based on AWS tags.
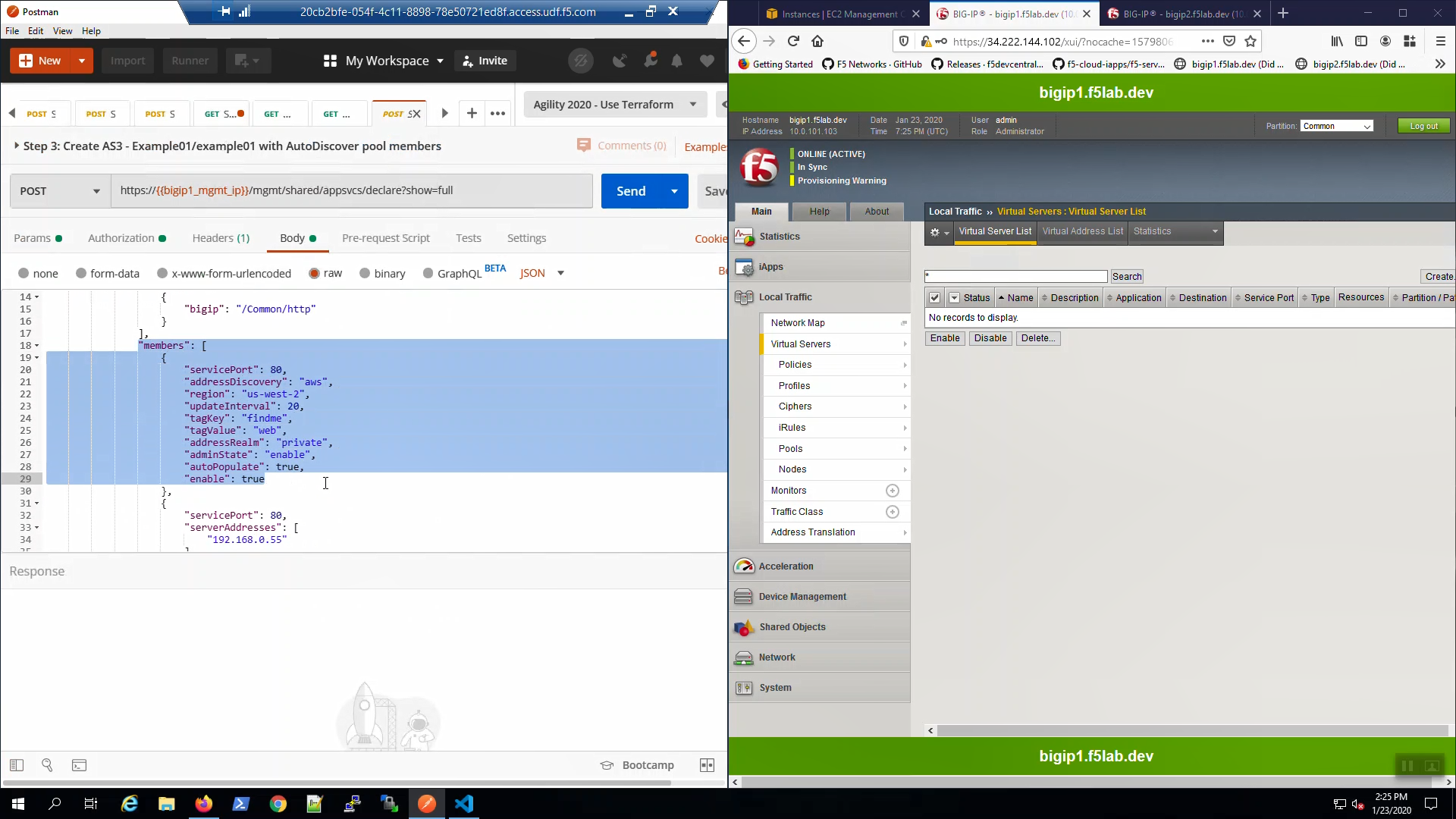
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 3: Example01/example01 with AutoDiscover pool members” => [Send].
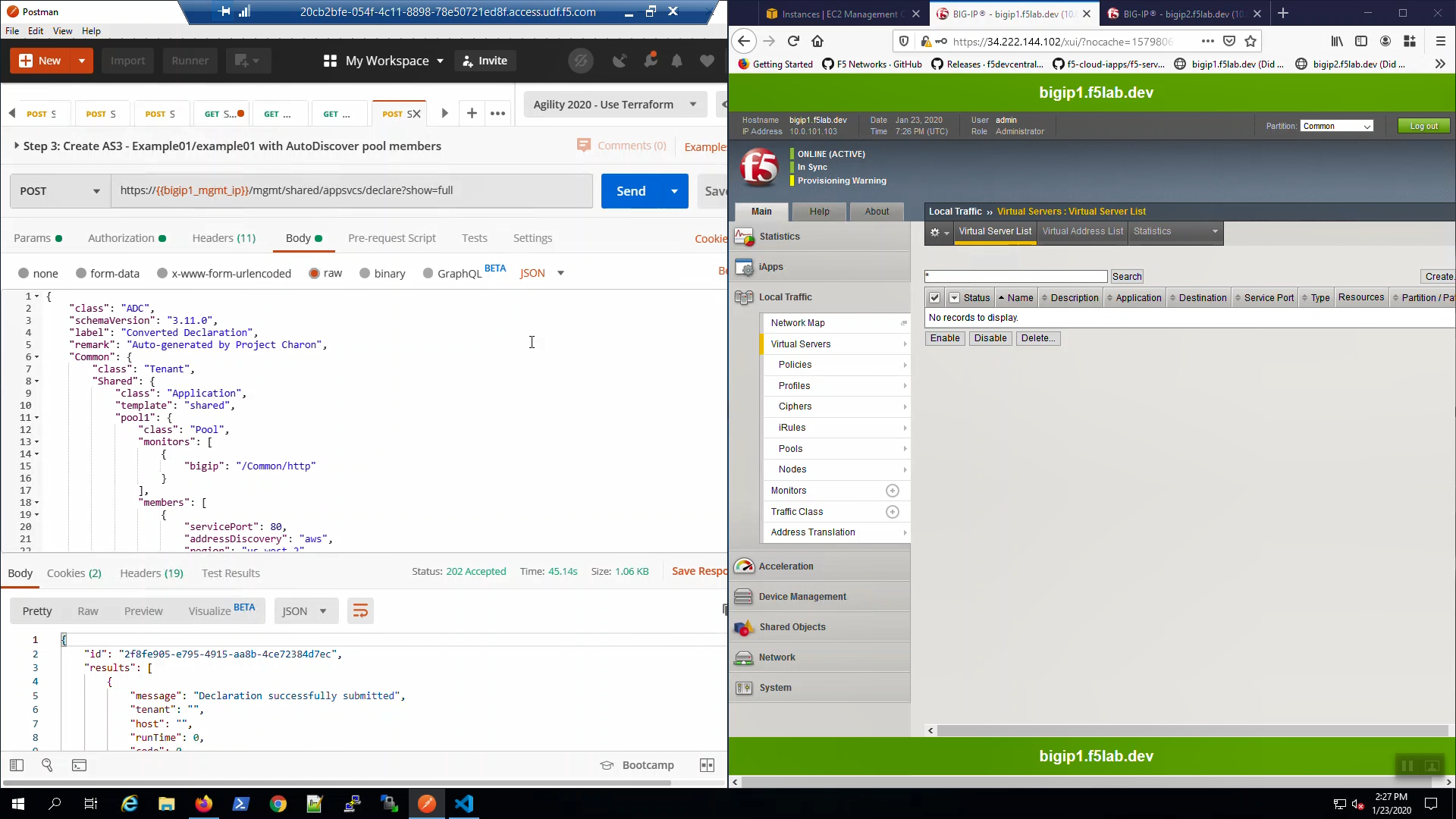
Change the HTTP method from POST to GET and click “Send”. You can do this often to track the status of the AS3 declaration in the Response. Status 202 indicates the declaration was successfully submitted and is being processed, Status 200 indicates the declaration has successfully completed.
Eventually, the status will be 200 OK. Our AS3 declaration has successfully created a pair of HTTP virtual servers.
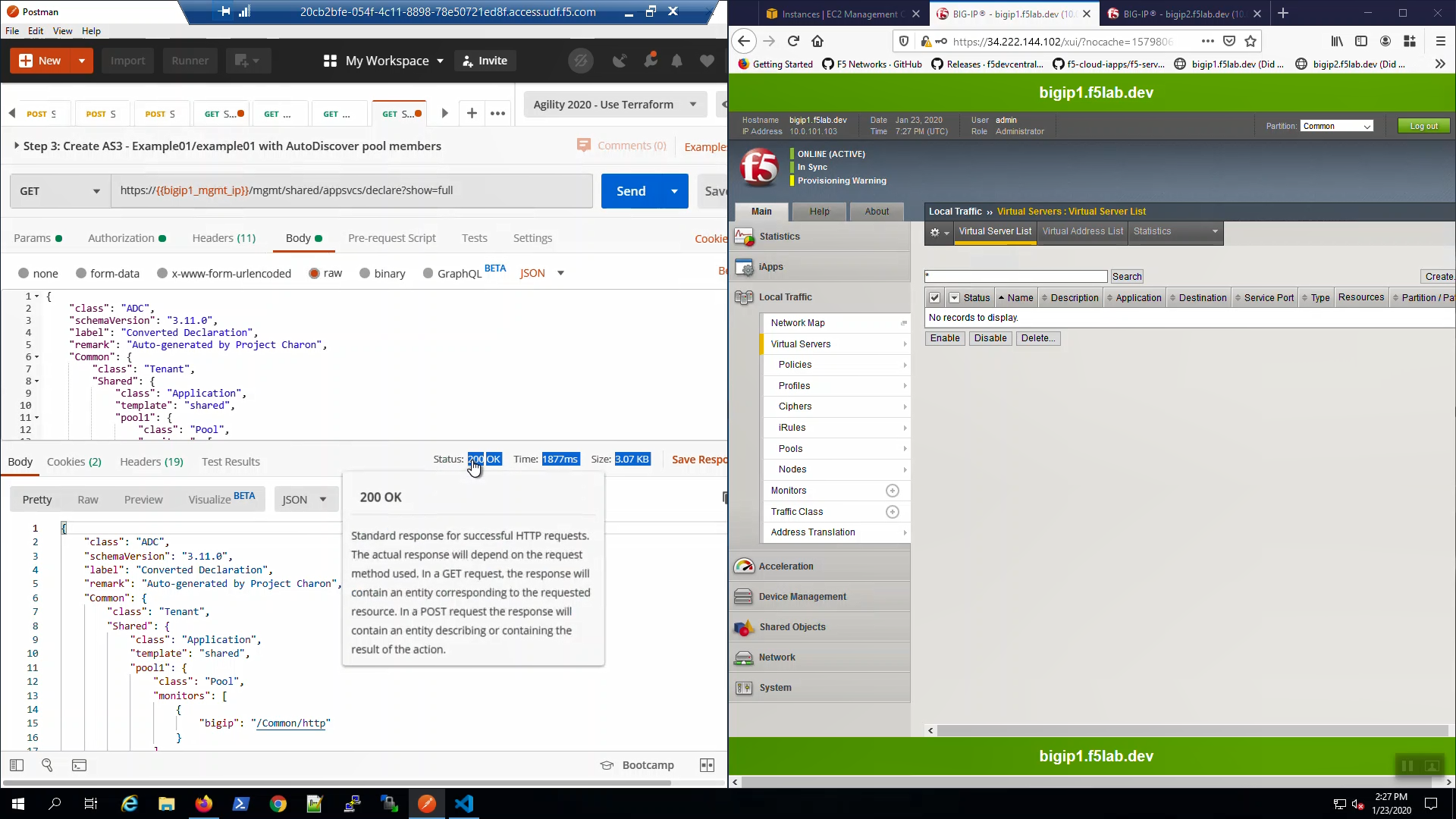
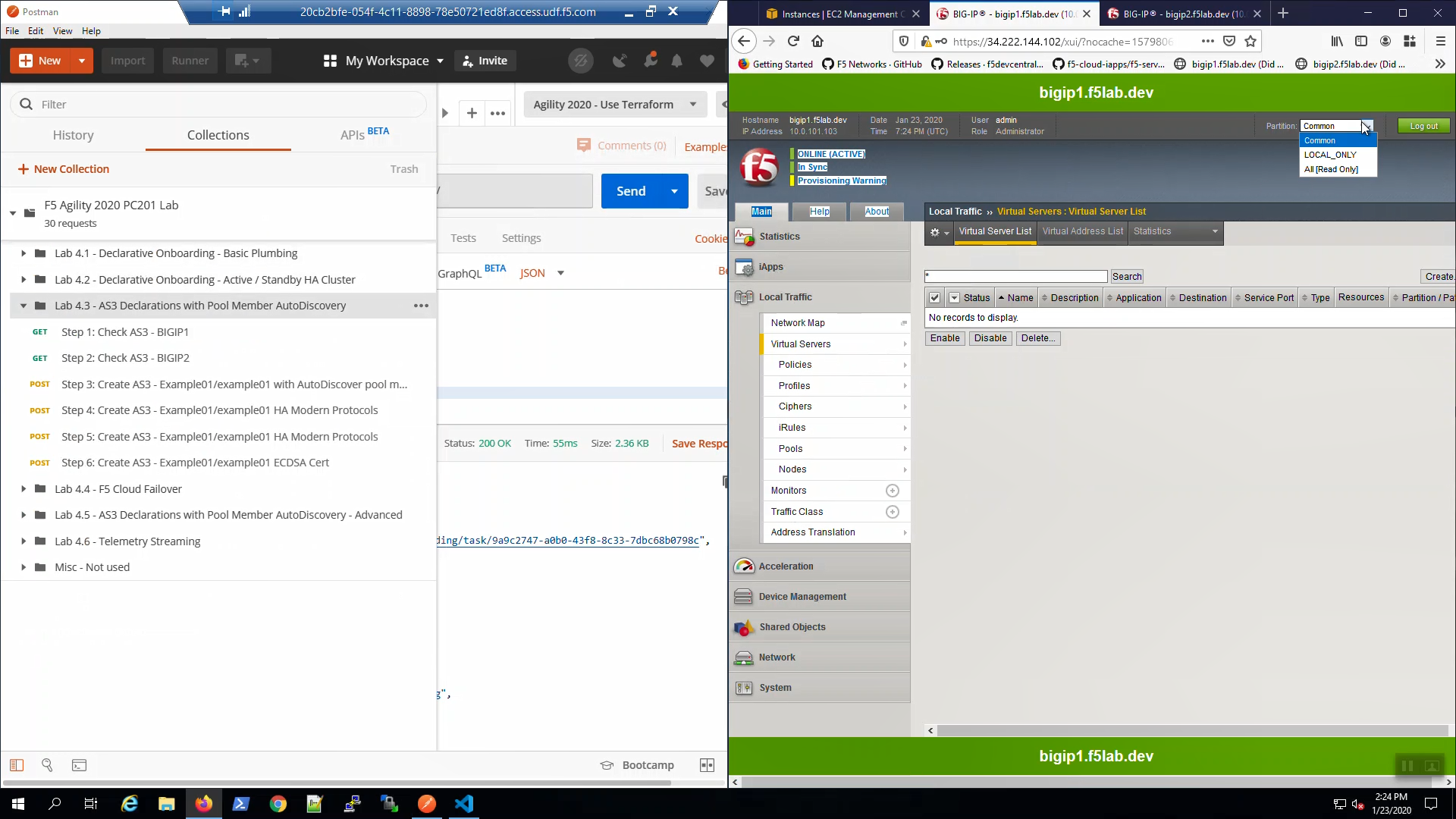
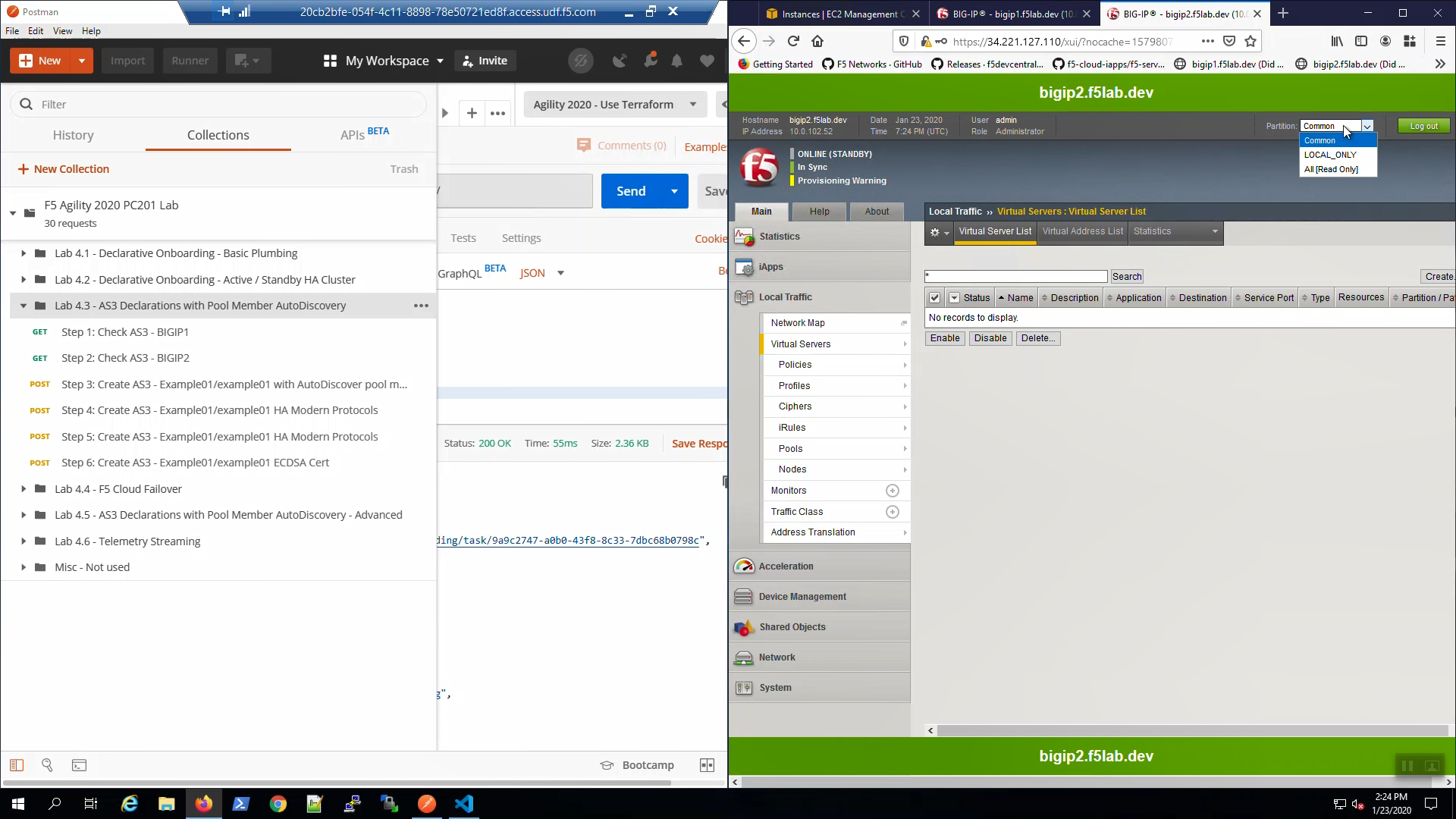
Big-IP1 => Local Traffic => Virtual Servers. Choose the “Example01” Partition from the Drop-down in the upper-right-hand corner. AS3 created two HTTP virtual servers: example01a and example01b.
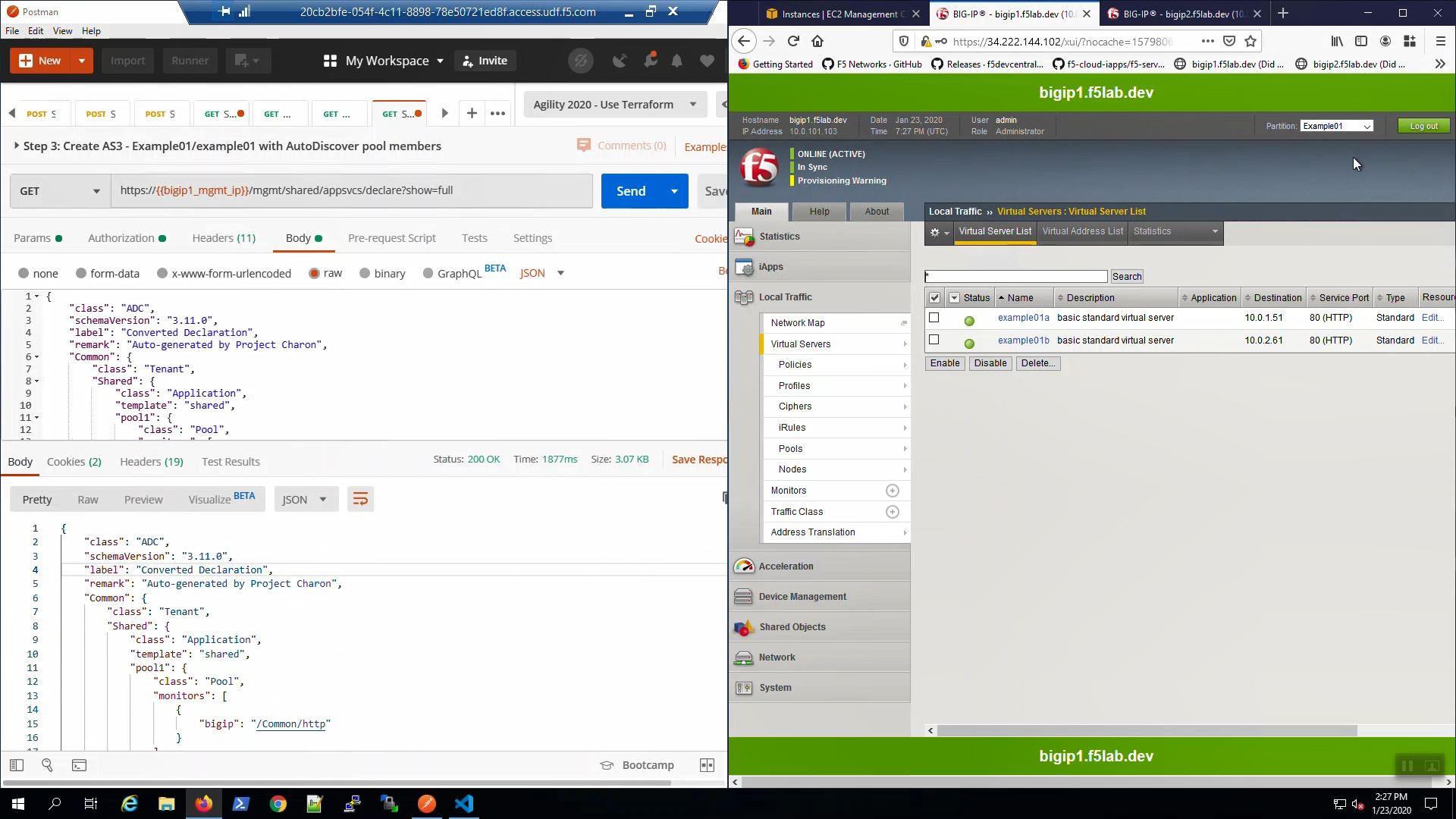
Big-IP1 => Local Traffic => Pools. Note “pool1”. AS3 used AWS instance tags to discover and auto-populate pool1 with two web servers.
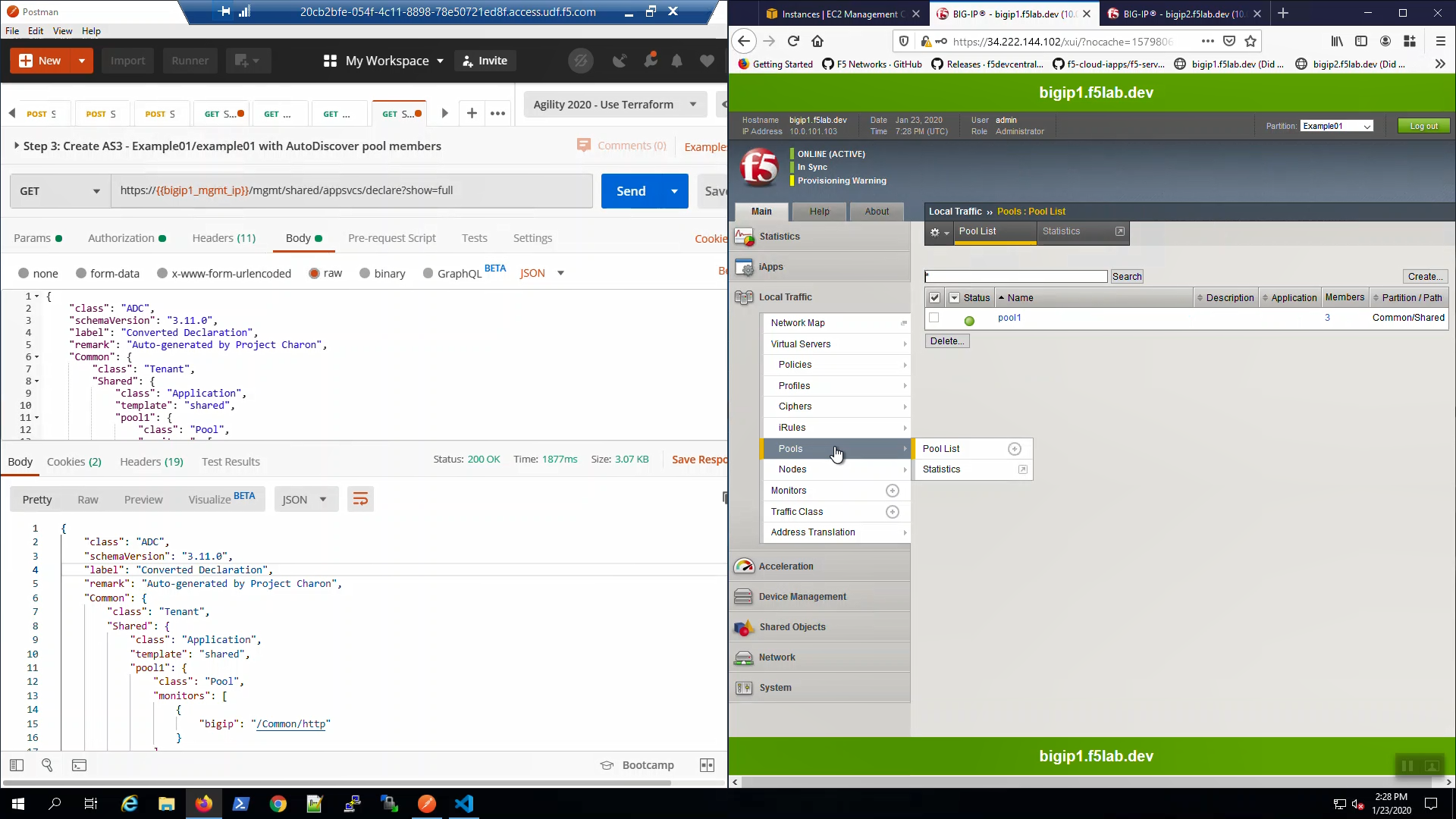
Big-IP2 => Local Traffic => Virtual Servers. Choose the “Example01” Partition from the Drop-down in the upper-right-hand corner. Even though you only POSTED an AS3 declaration to Big-IP1, Config Sync replicated the Virtual Servers and all supporting configuration objects (pools, profiles, etc.) to Big-IP2.
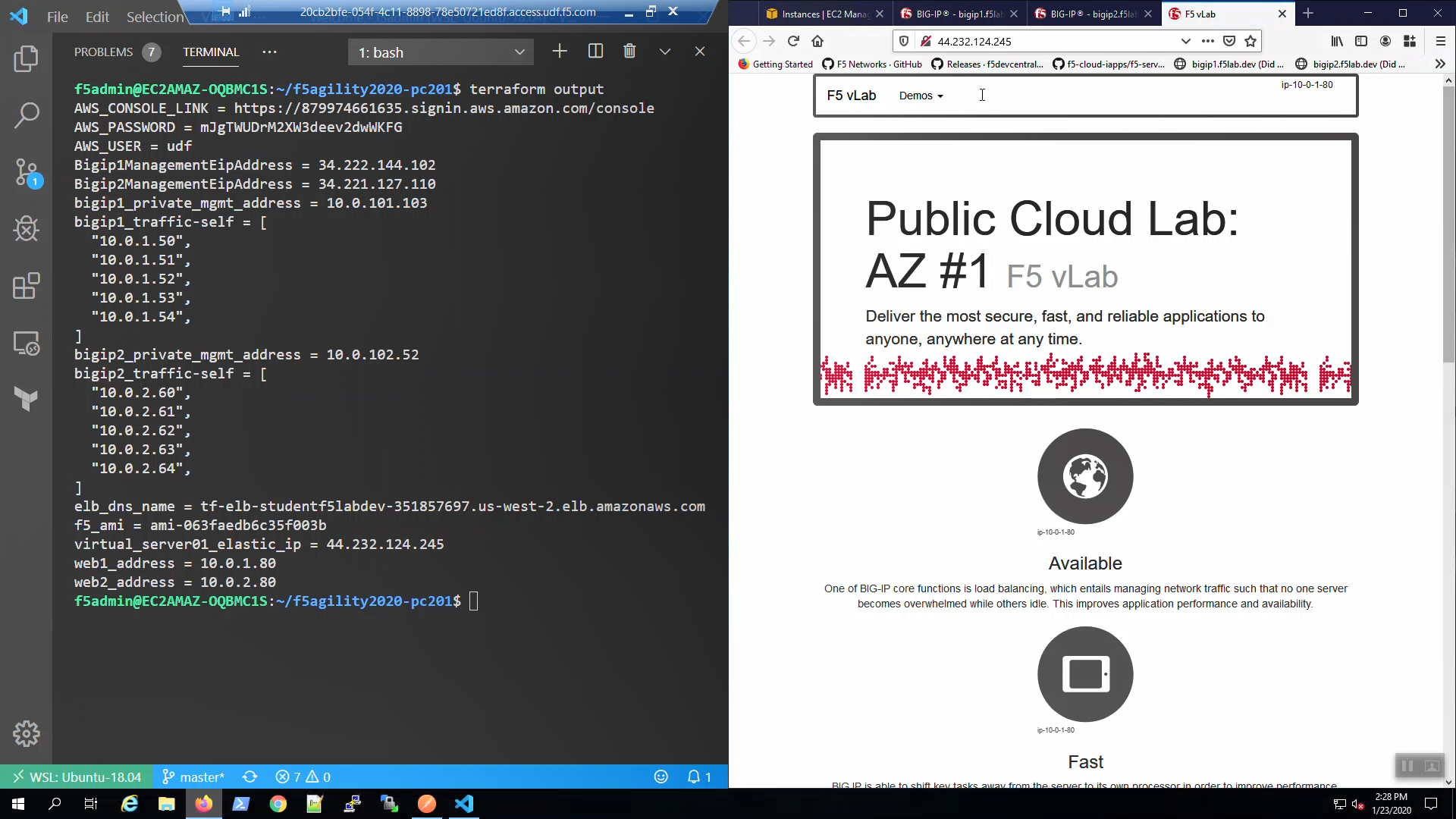
From the Visual Studio Code Terminal, note the value of virtual_server01_elastic_ip.
terraform output virtual_server01_elastic_ip
Open a new browser tab. Connect via HTTP to virtual_server01_elastic_ip.
2.6.4. Enable modern protocols such as HTTP/2 and TLS 1.3 with AS3 and Service Discovery¶
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 4: Create AS3 - Example01/example01 HA Modern Protocols”. => [Send].
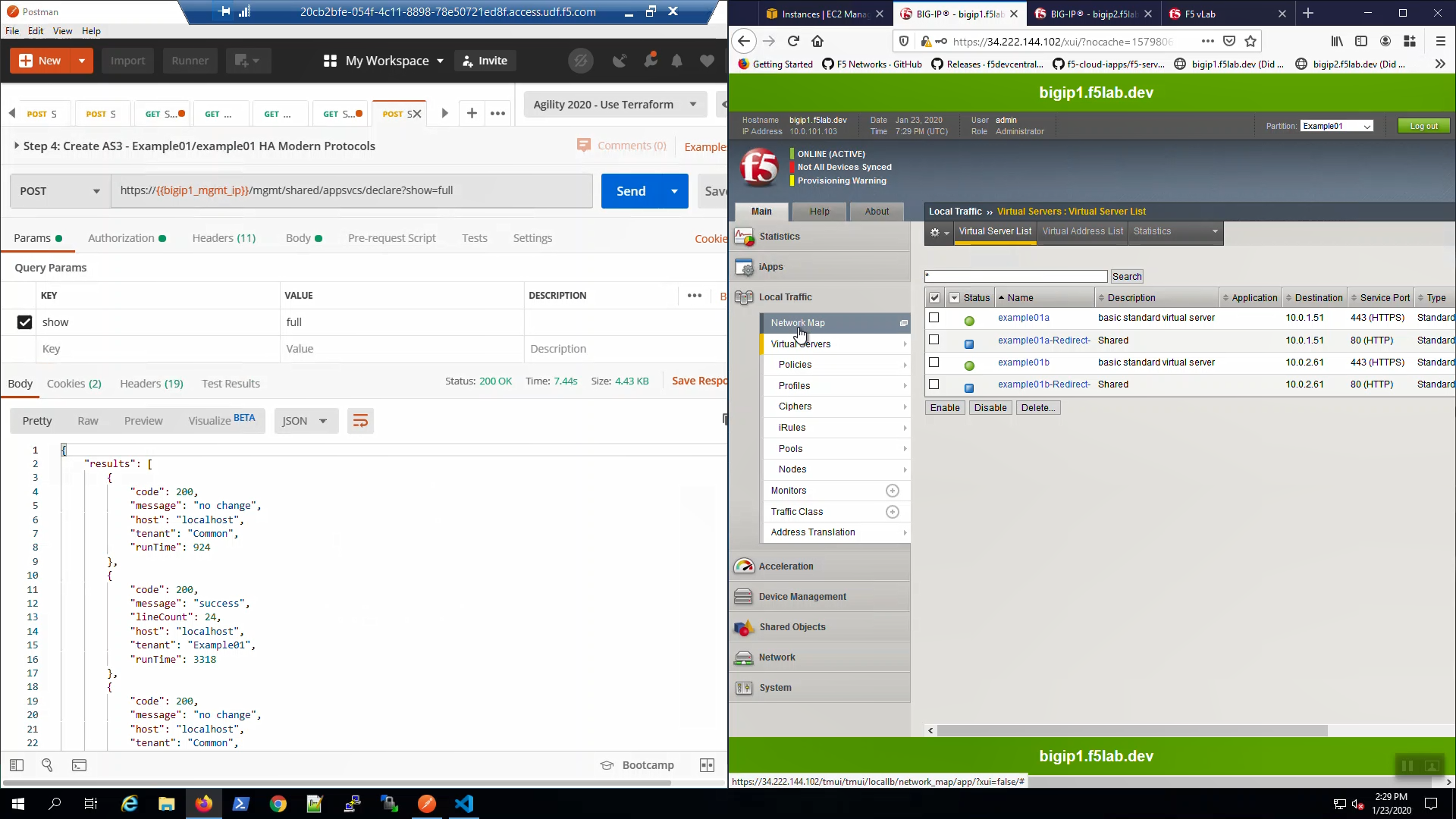
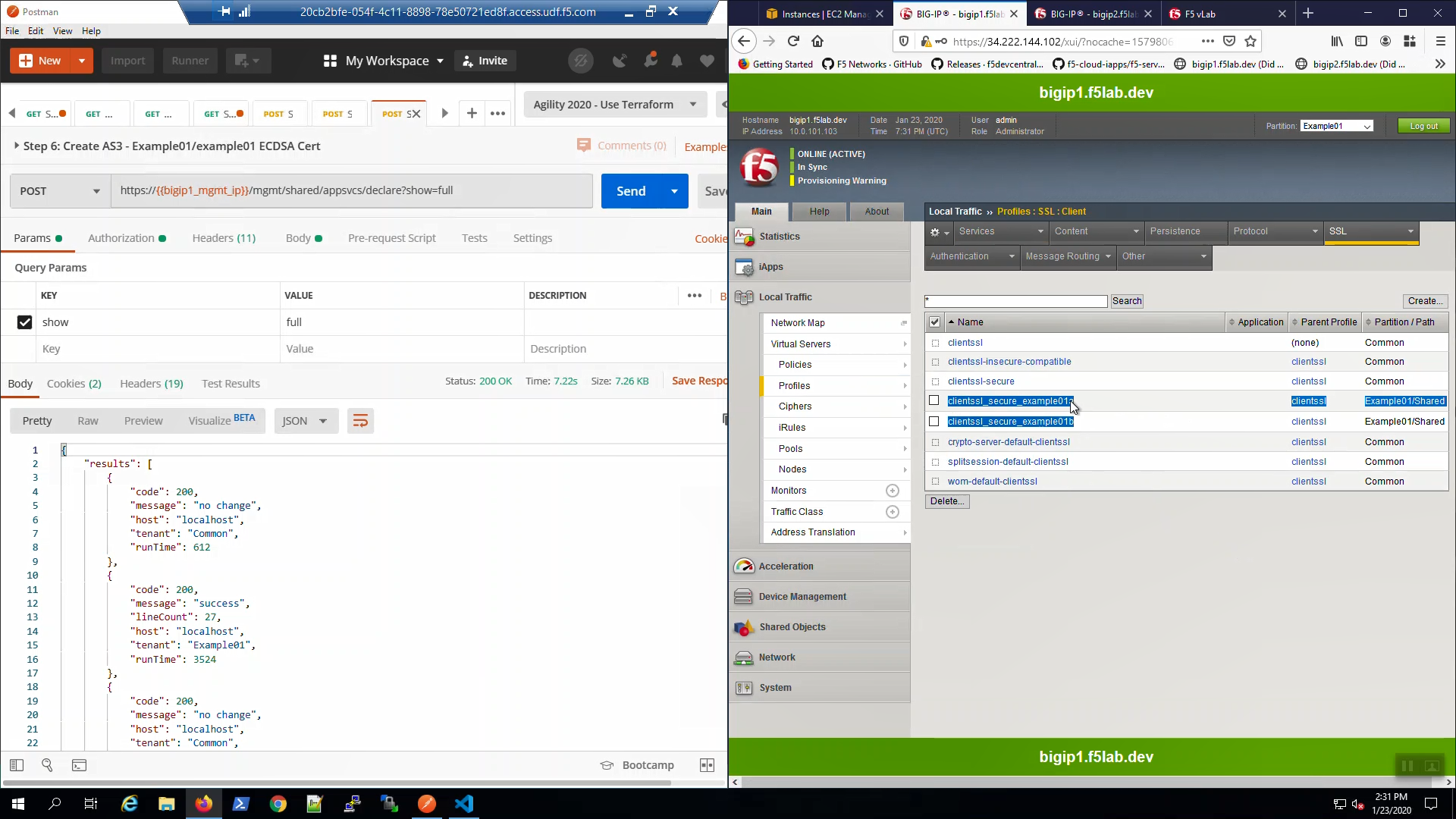
Big-IP1 => Local Traffic => Virtual Servers => Click on “example01a”. Scroll down to the SSL Profile (Client). AS3 created and applied a custom SSL profile to our HTTPS virtual servers.
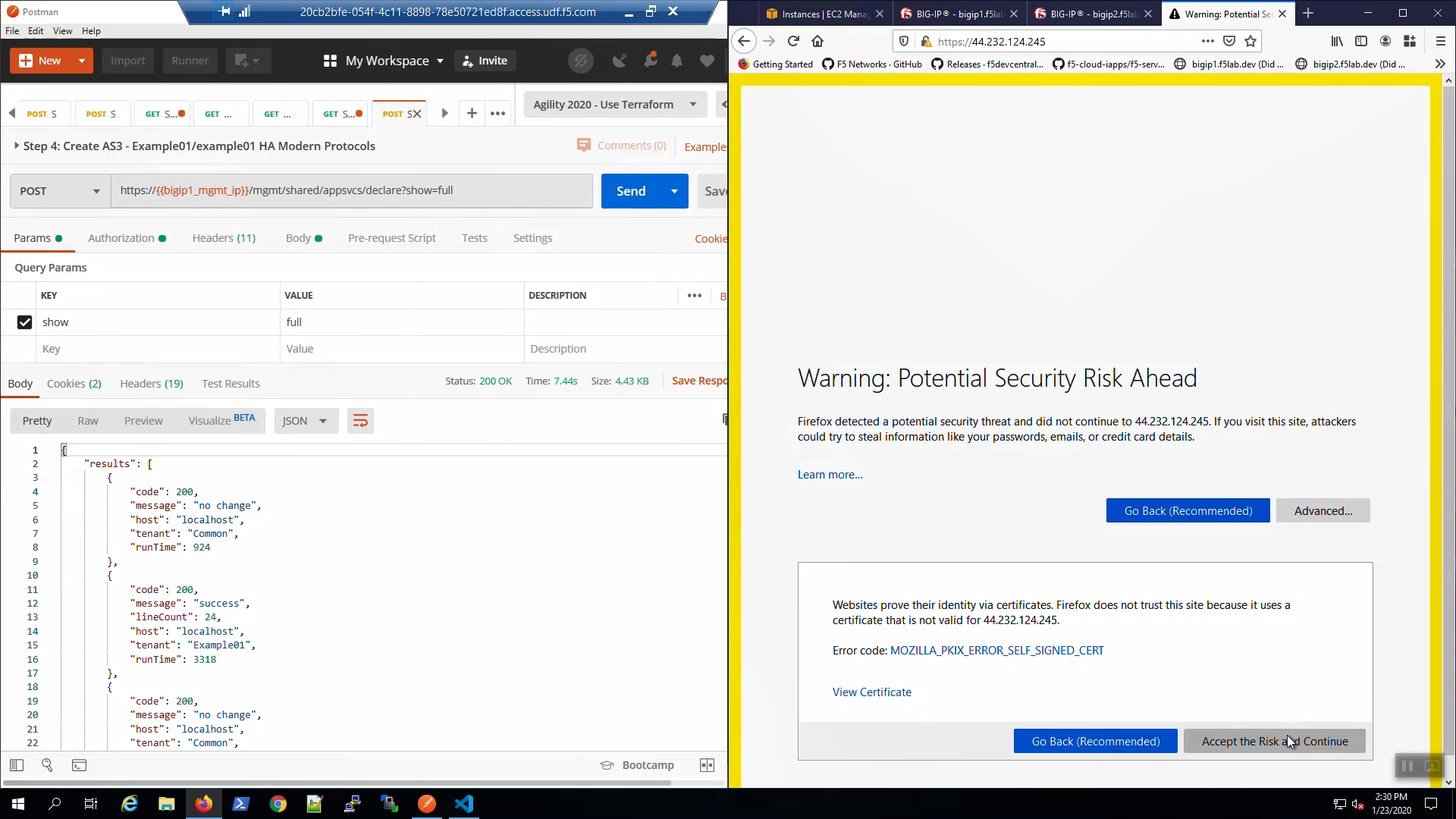
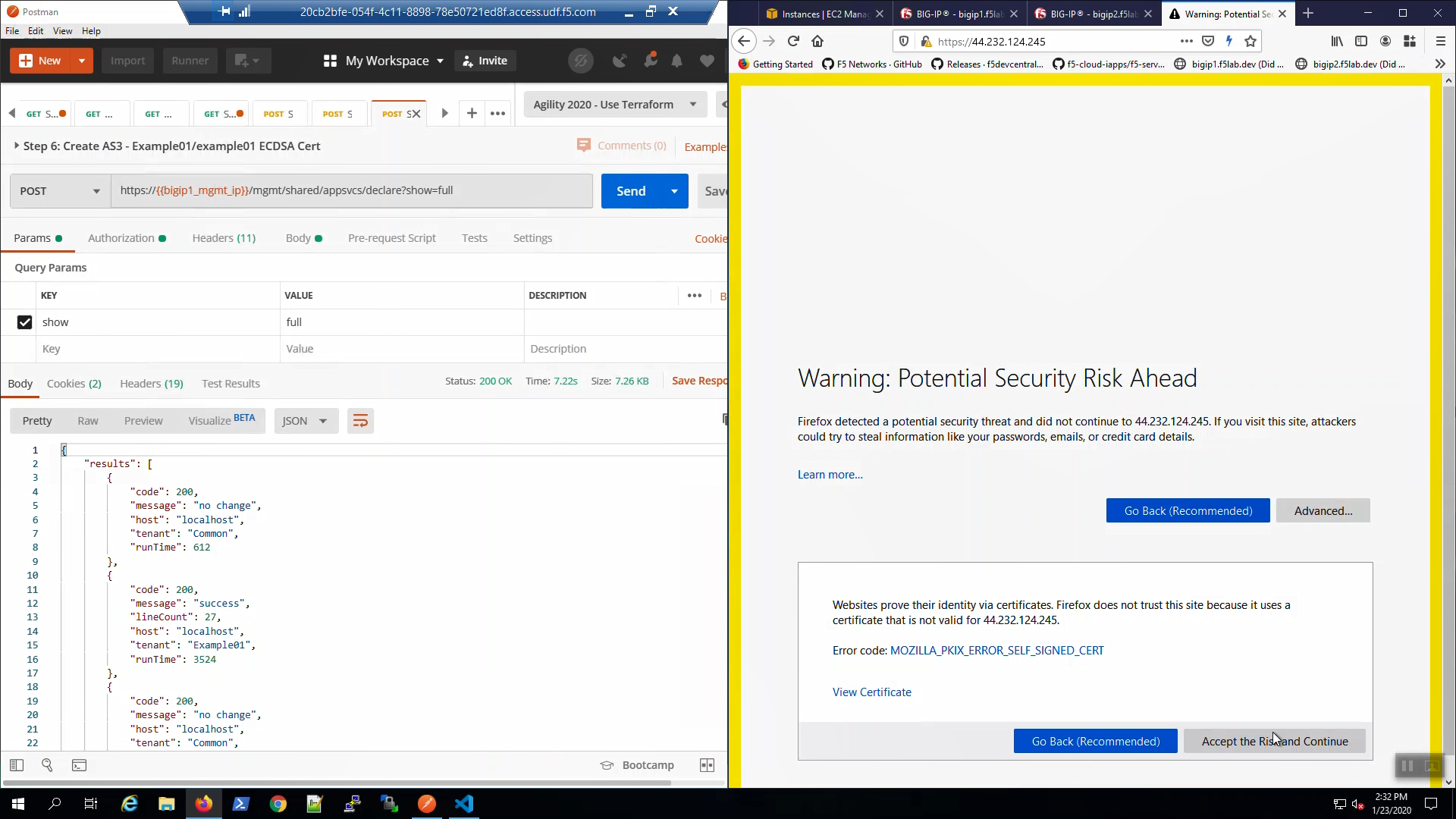
Open a new browser tab. Connect via HTTPS to virtual_server01_elastic_ip. We are using self-signed certificates in the lab. Bypass the TLS warnings. “Accept the Risk and Continue”.
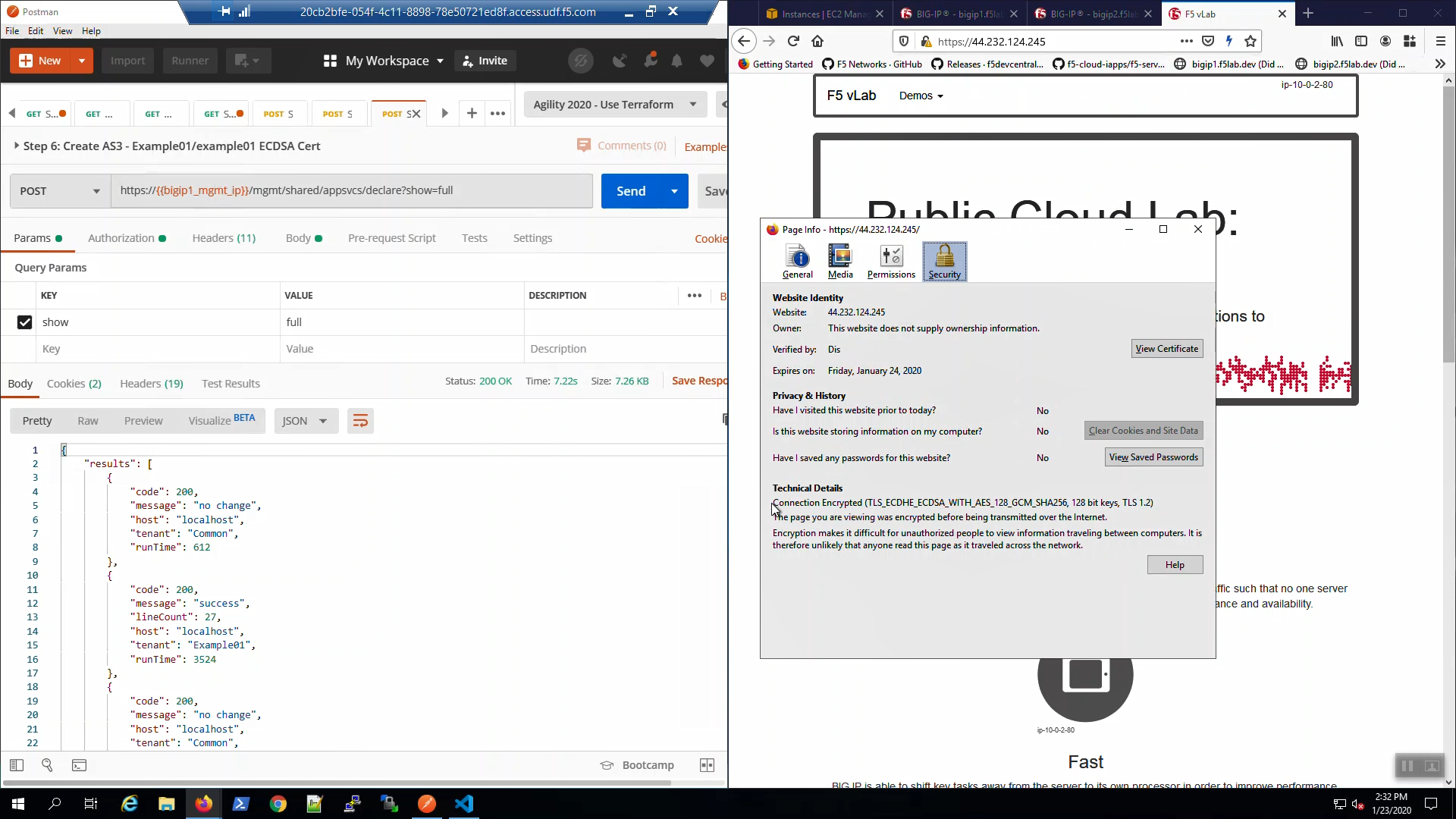
From the browser, note the ciphers used: TLS 1.2. We’ll upgrade to TLS 1.3 with ECDSA certs shortly.
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 5: Create AS3 - Example01/example01 HA Modern Protocols”. => [Send].
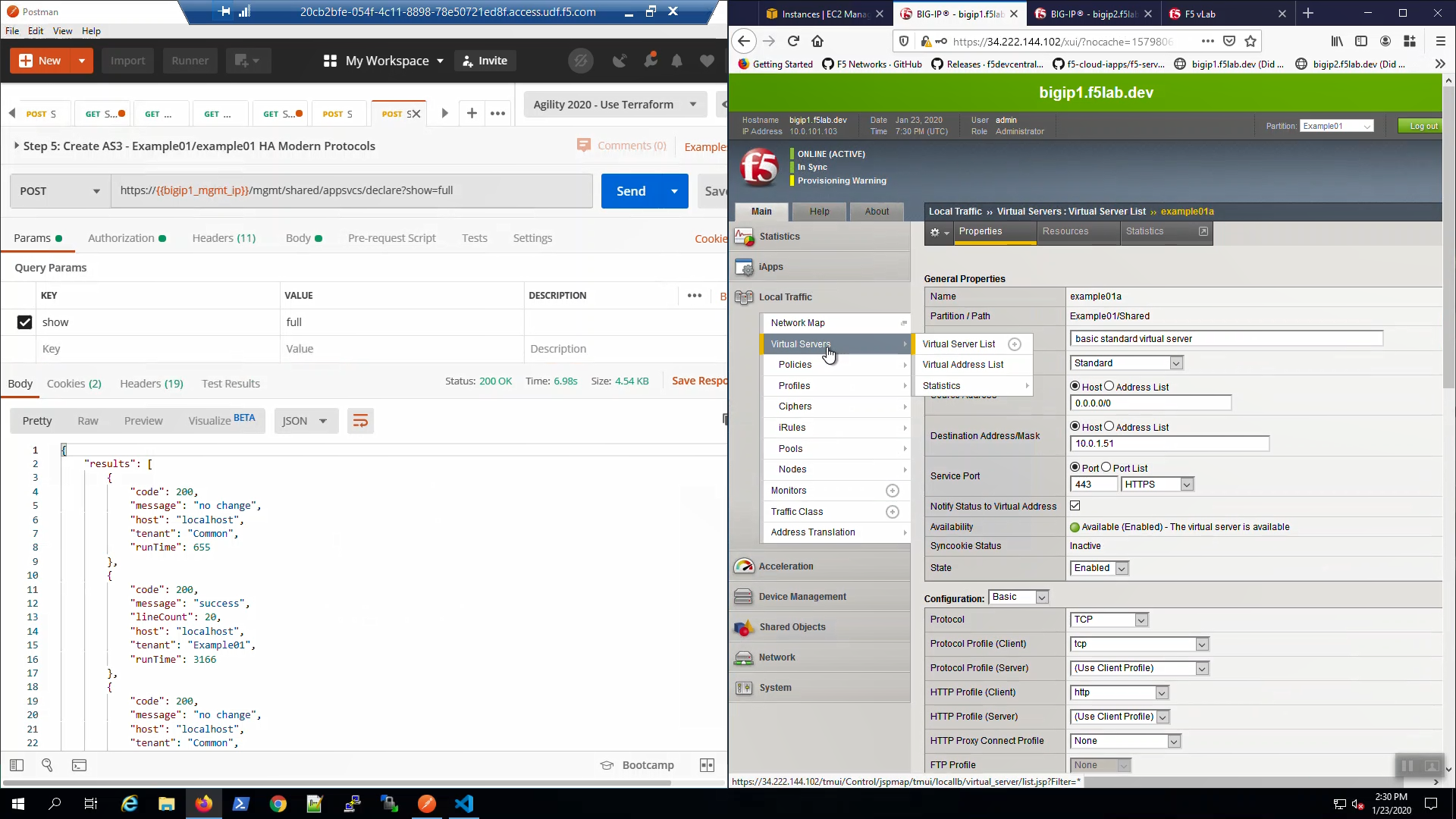
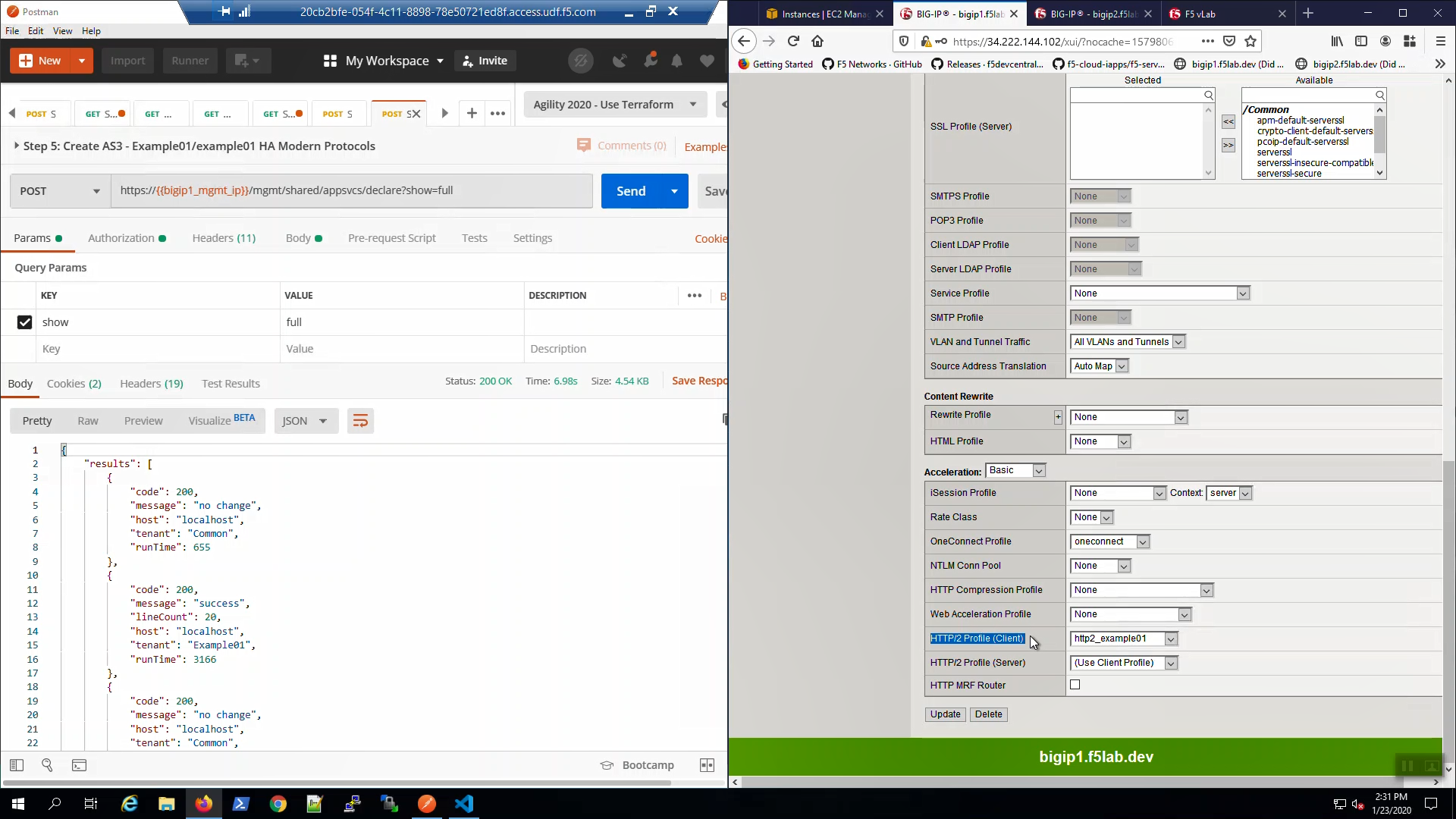
Big-IP1 => Local Traffic => Virtual Servers => Click on “example01a”. Scroll down to the HTTP/2 Profile (Client). Note we have enabled HTTP/2.
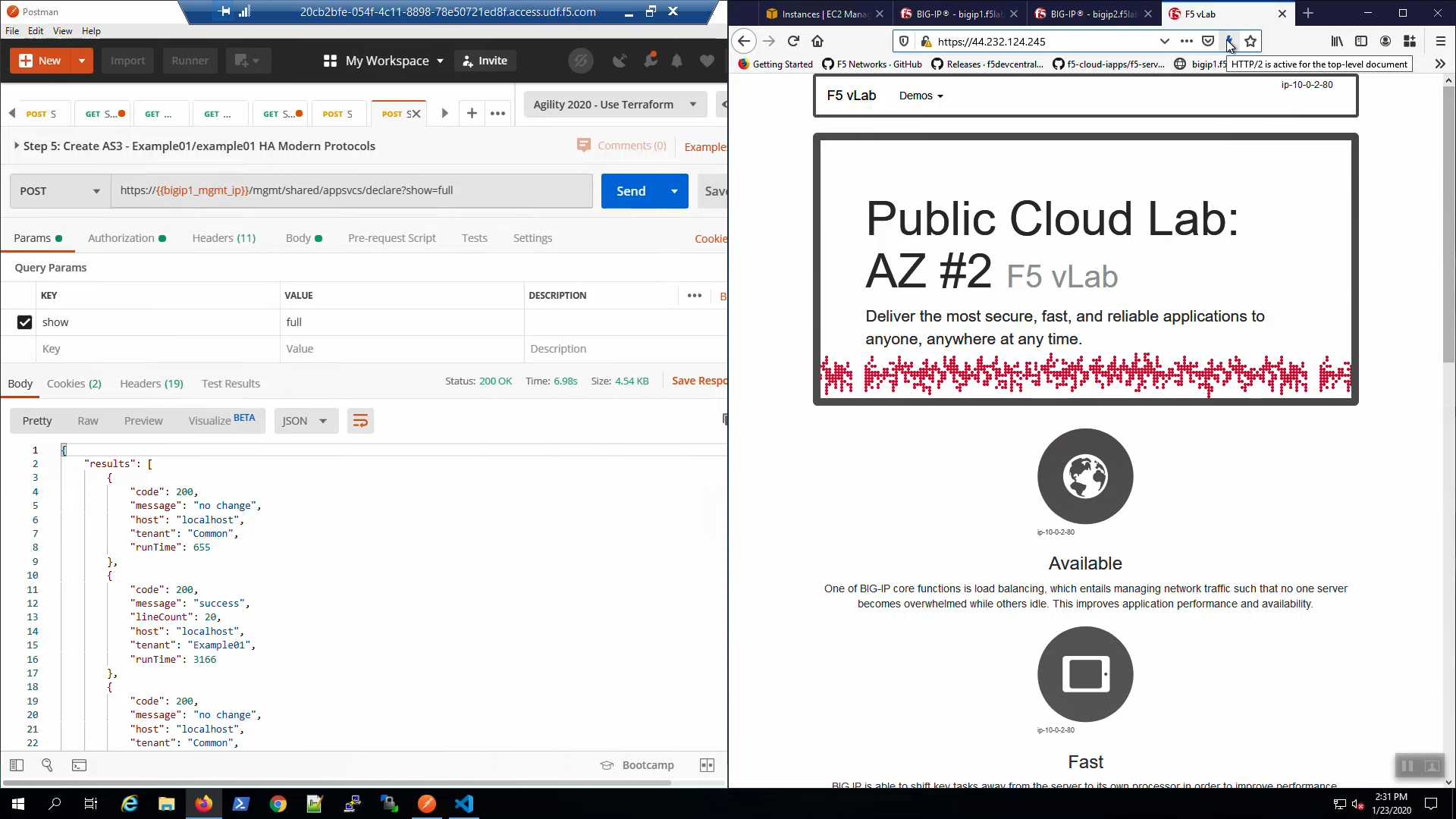
From the browser, in the tab with the example HTTPS application, hit [CTRL] + [F5] a few times to refresh the page. Hover over the lightning bolt icon on the right-hand side of the URL bar. Note: “HTTP/2 is active for the top-level document”.
Attention
In the following examples, the cert and keys are stored as Postman environment variables. This is for illustrative purposes only. In a secure production environment you must incorporate a proper secrets management solution.
From Postman, “Lab - AS3 Declarations with Pool Member AutoDiscovery” => “Step 6: Create AS3 - Example01/example01 ECDSA Cert”. => [Send].
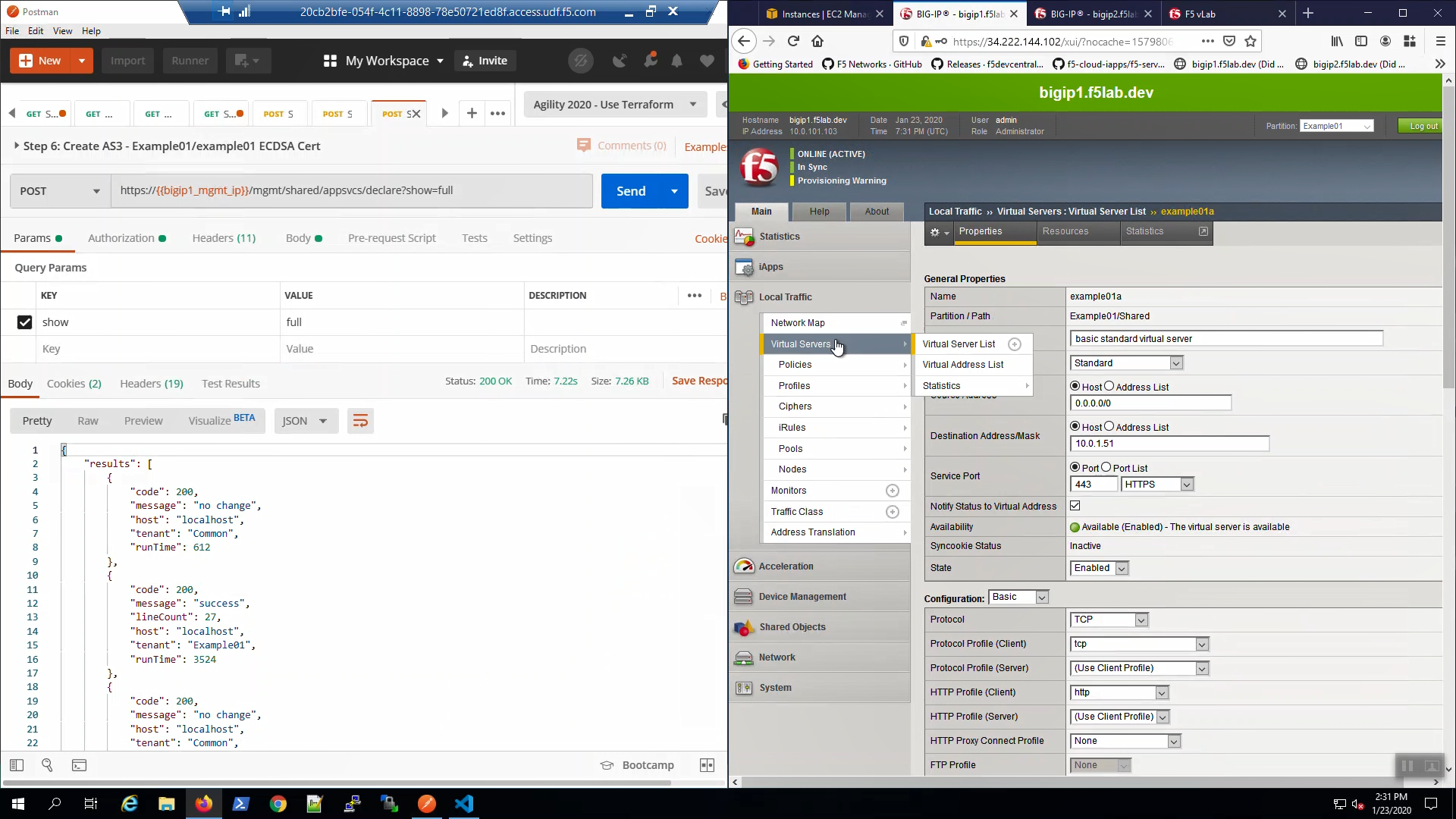
Big-IP1, “Local Traffic” => “Profiles” => “SSL” => “Client”. Note “clientssl_secure_example01a” “clientssl_secure_example01b” profiles created and applied to the example01a and example01b virtual servers.
From the browser, in the tab with the example HTTPS application, hit [CTRL] + [F5] a few times to refresh the page. We are using self-signed certificates in the lab. Bypass the TLS warnings. “Accept the Risk and Continue”.
Click on the padlock icon on the left-hand side of the URL bar and note the ciphers used: ECDSA enabled but still TLS 1.2.
Big-IP1, “Local Traffic” => “Profiles” => “SSL” => “Client”. Select the “clientssl_secure_example01a” profile. Modify the profile to support TLS 1.3.
- Ciphers => (*)Cipher Group => f5-default.
- Options List => Select “No TLSv1.3” and [Disable]
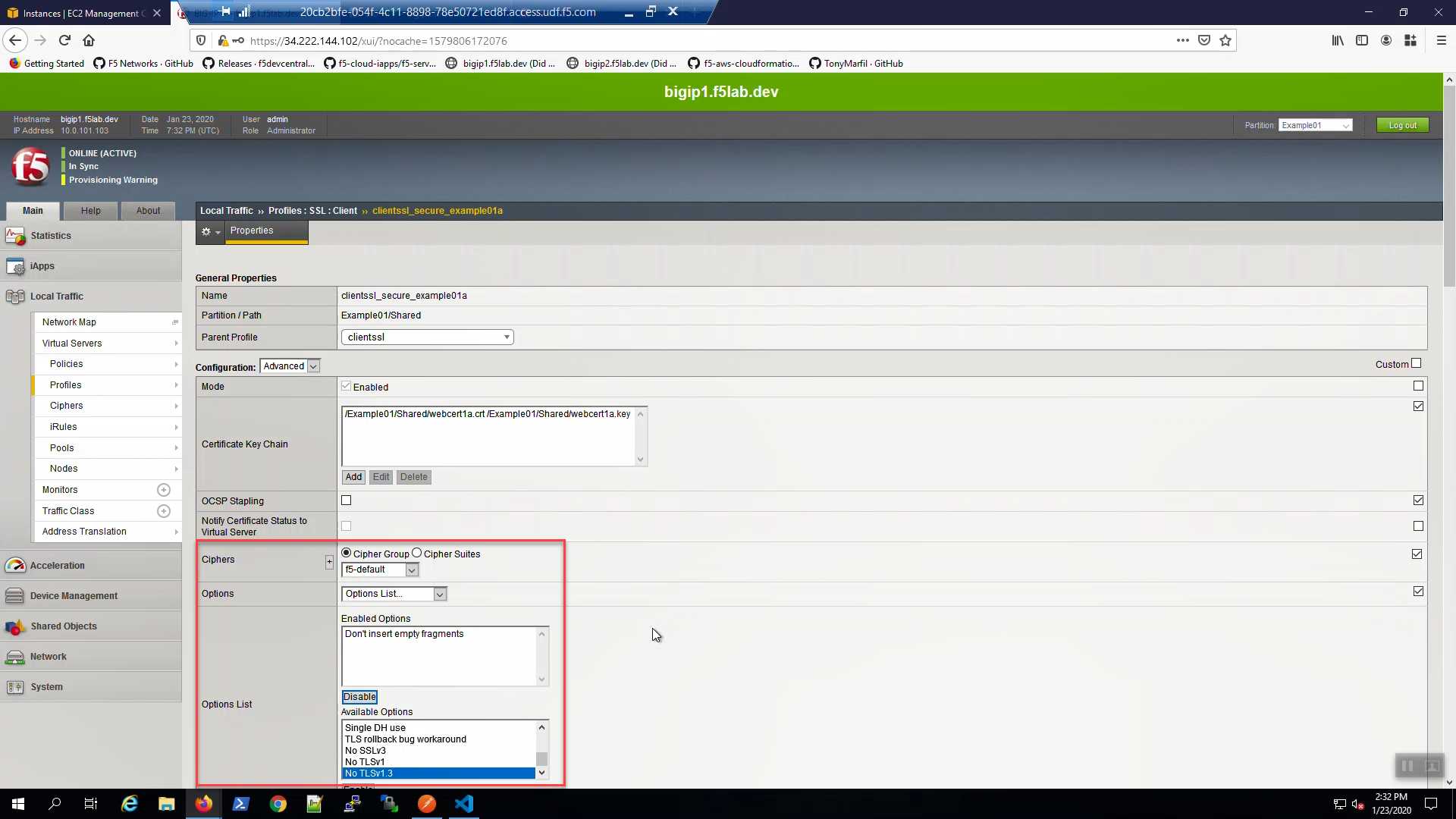
Scroll down and [Update].
Do the same for the “clientssl_secure_example01b” profile.
Big-IP1, “Local Traffic” => “Profiles” => “SSL” => “Client”. Select the “clientssl_secure_example01b” profile. Modify the profile to support TLS 1.3.
- Ciphers => (*)Cipher Group => f5-default.
- Options List => Select “No TLSv1.3” and [Disable]
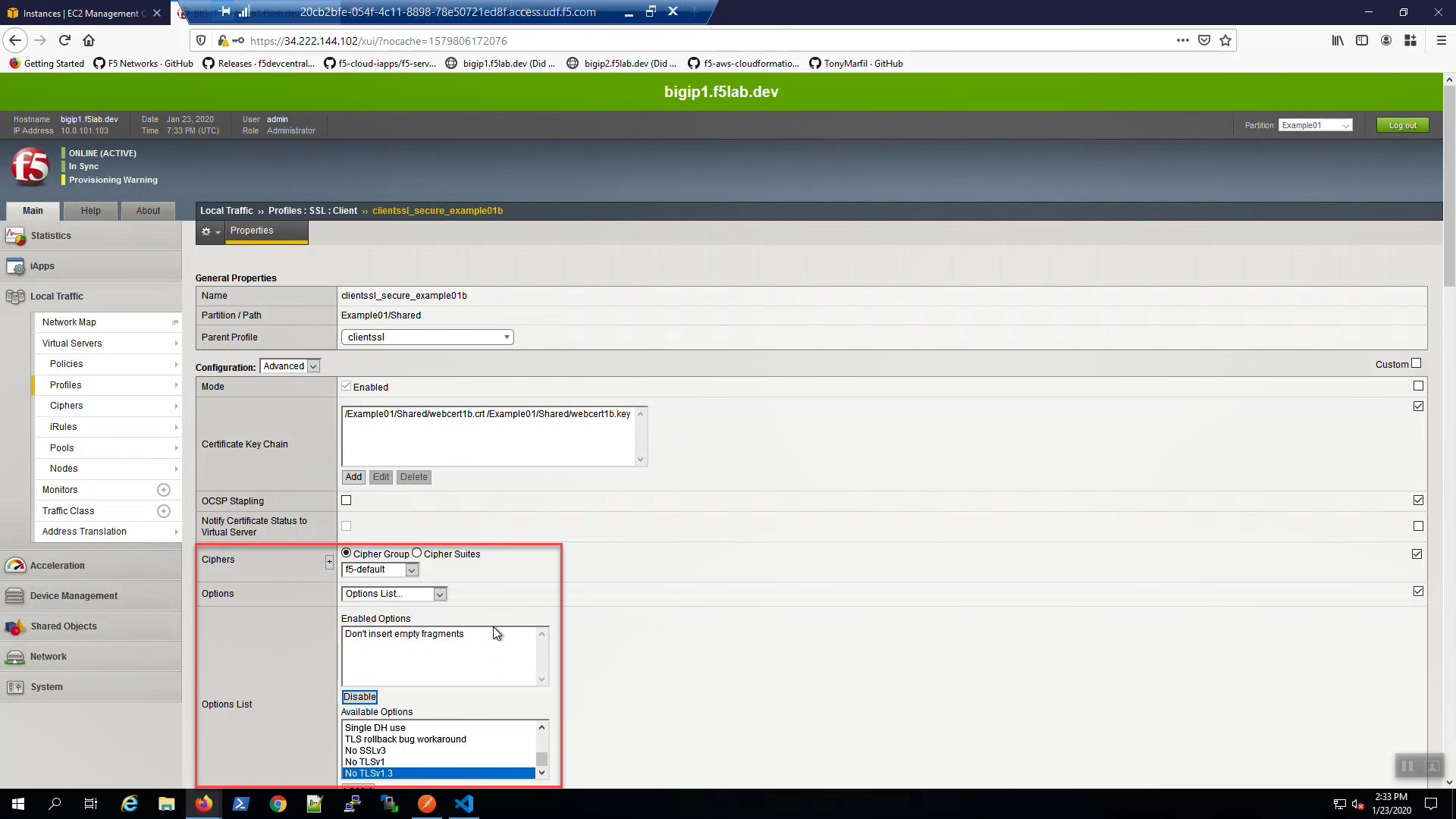
Scroll down and [Update].
From the browser, in the tab with the example HTTPS application, hit [CTRL] + [F5] a few times to refresh the page. Click on the padlock icon on the left-hand side of the URL bar and note the ciphers used: ECDSA enabled and TLS 1.3.