F5 Public Cloud Solutions > 5. F5 WAF in AWS > 5.5. Logging to CloudWatch Source | Edit on
5.5.1. LTM Request Logging to CloudWatch¶
From the Super-NetOps terminal, run the handy lab-info utility. Confirm that “MCPD is up, System Ready” for all three of your instances.
lab-info
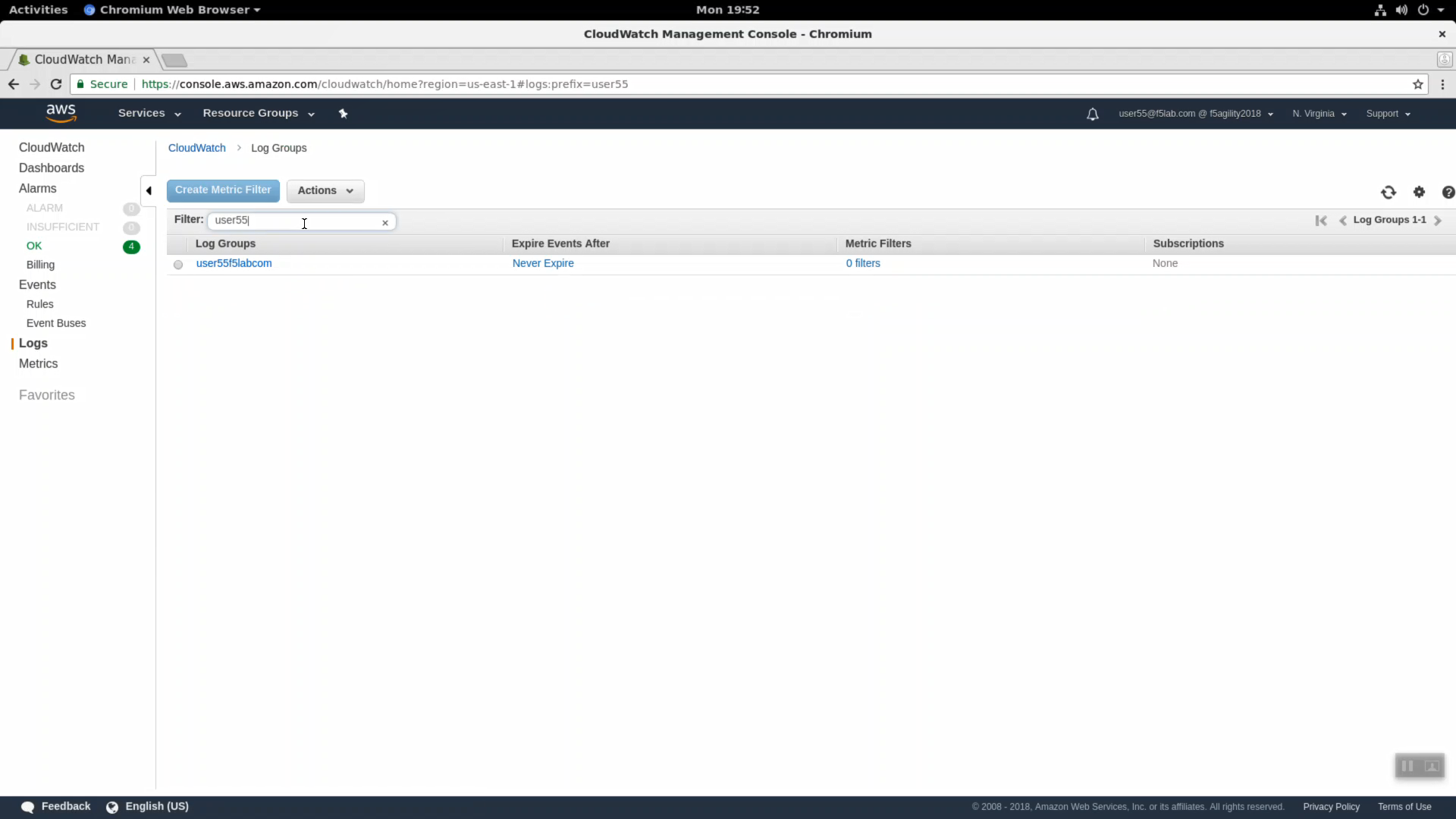
From the AWS management console, navigate to Services => Management Tools => CloudWatch => Log Groups. In the search filter enter your username (i.e. user55). Terraform created a Log Group for you.
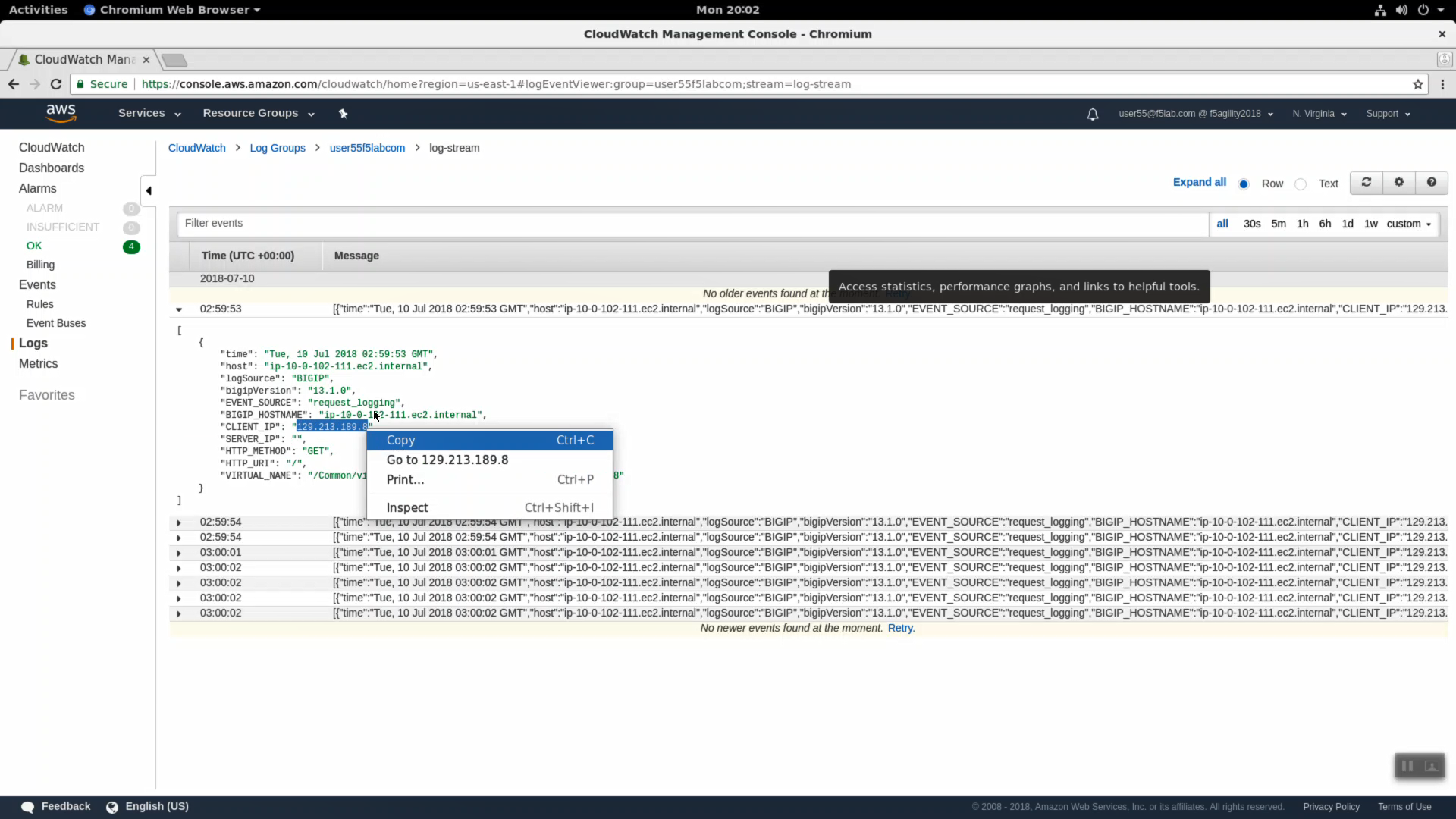
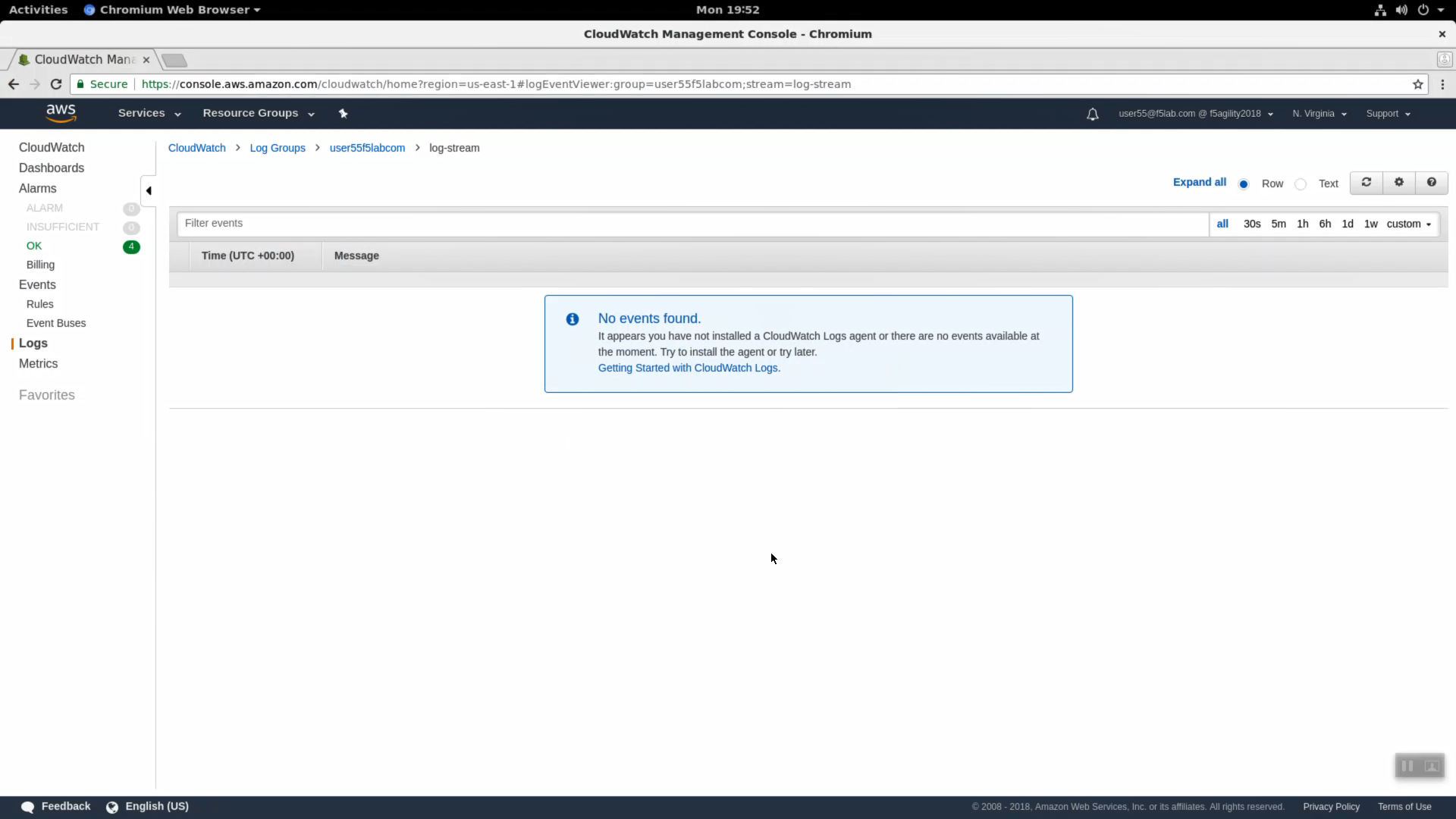
Click on your log group. Click on your log stream named “log-stream”. Notice the Message column has no messages.
Right-click and copy your log group name (i.e. user55labcom). Save in notepad or your preferred text editor / note taking method for later use.
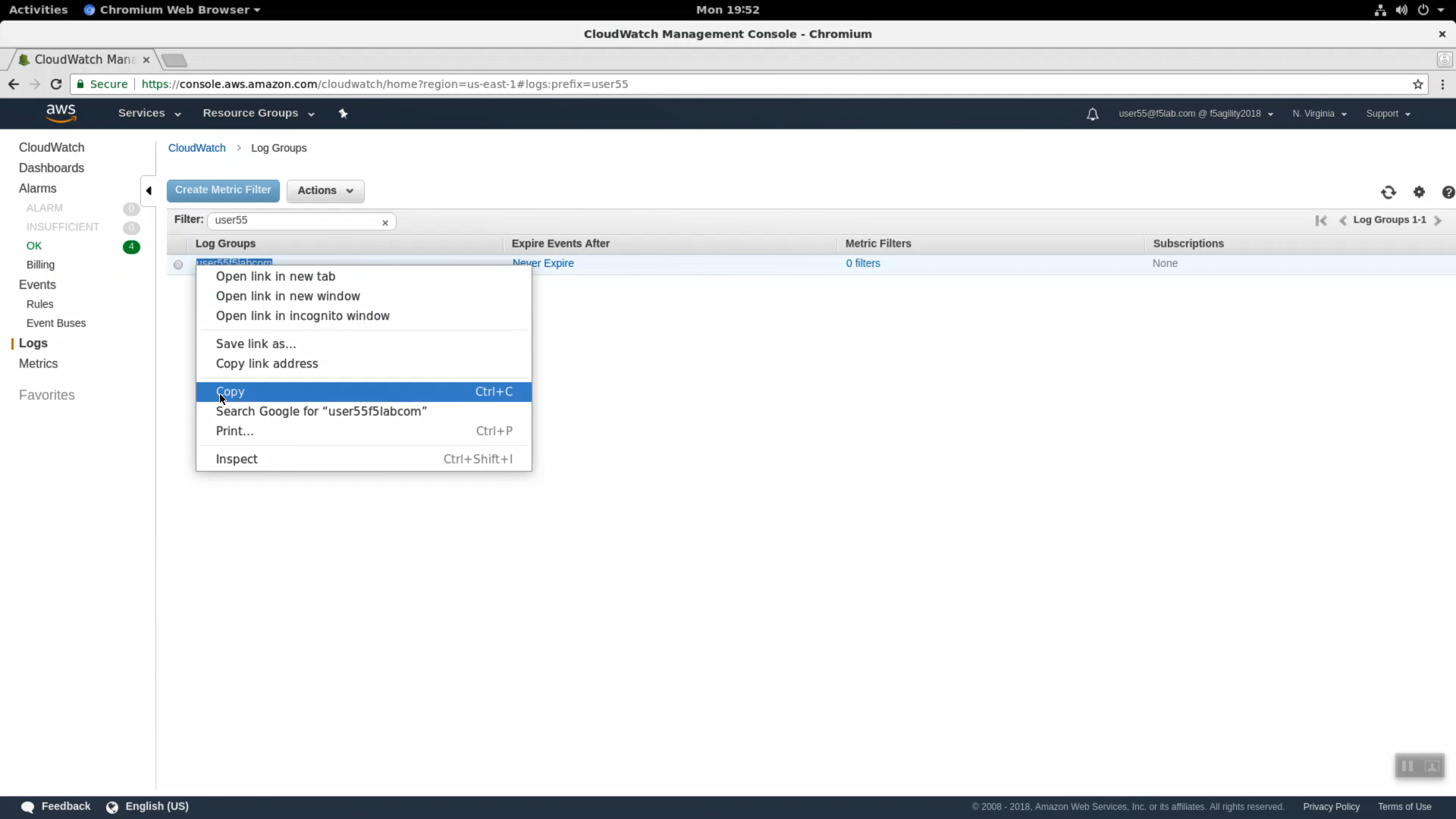
For convenience working through the next few steps, split your screen into two halves: Super-NetOps terminal on the left and the Firefox or Chrome browser on the right. On a standard Windows US/English Windows keyboard you can split the screen with <Windows Key + left arrow> and <Windows Key + right arrow>.
From your Super-NetOps terminal, there are multiple ways to see your AWS access keys. You can echo the environment variables:
echo $AWS_ACCESS_KEY_ID
echo $AWS_SECRET_ACCESS_KEY
…or you can cat the hidden ~/.aws/config file:
cat ~/.aws/config
Copy your AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY values. Save in notepad or your preferred text editor / note taking method for later use.
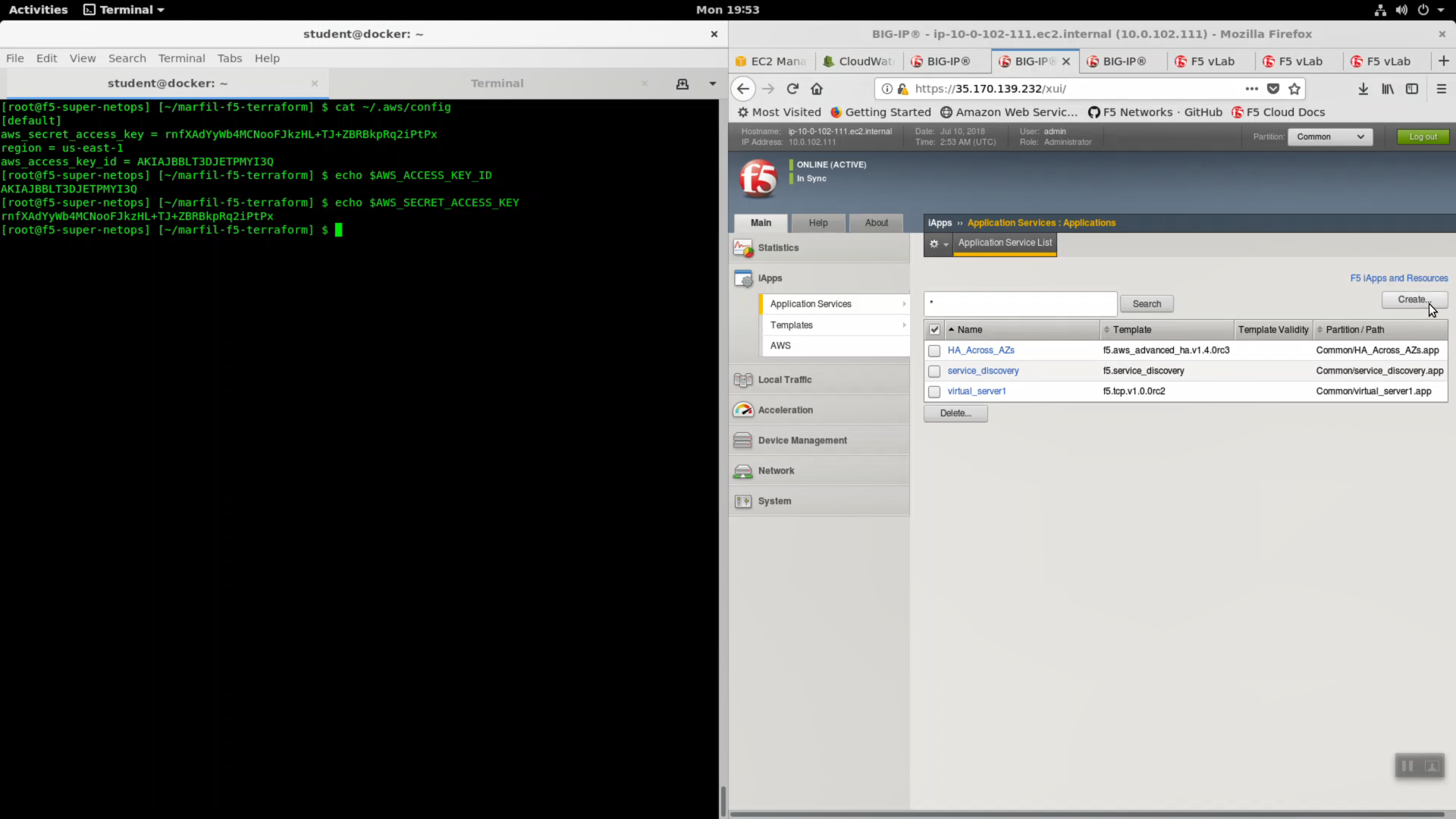
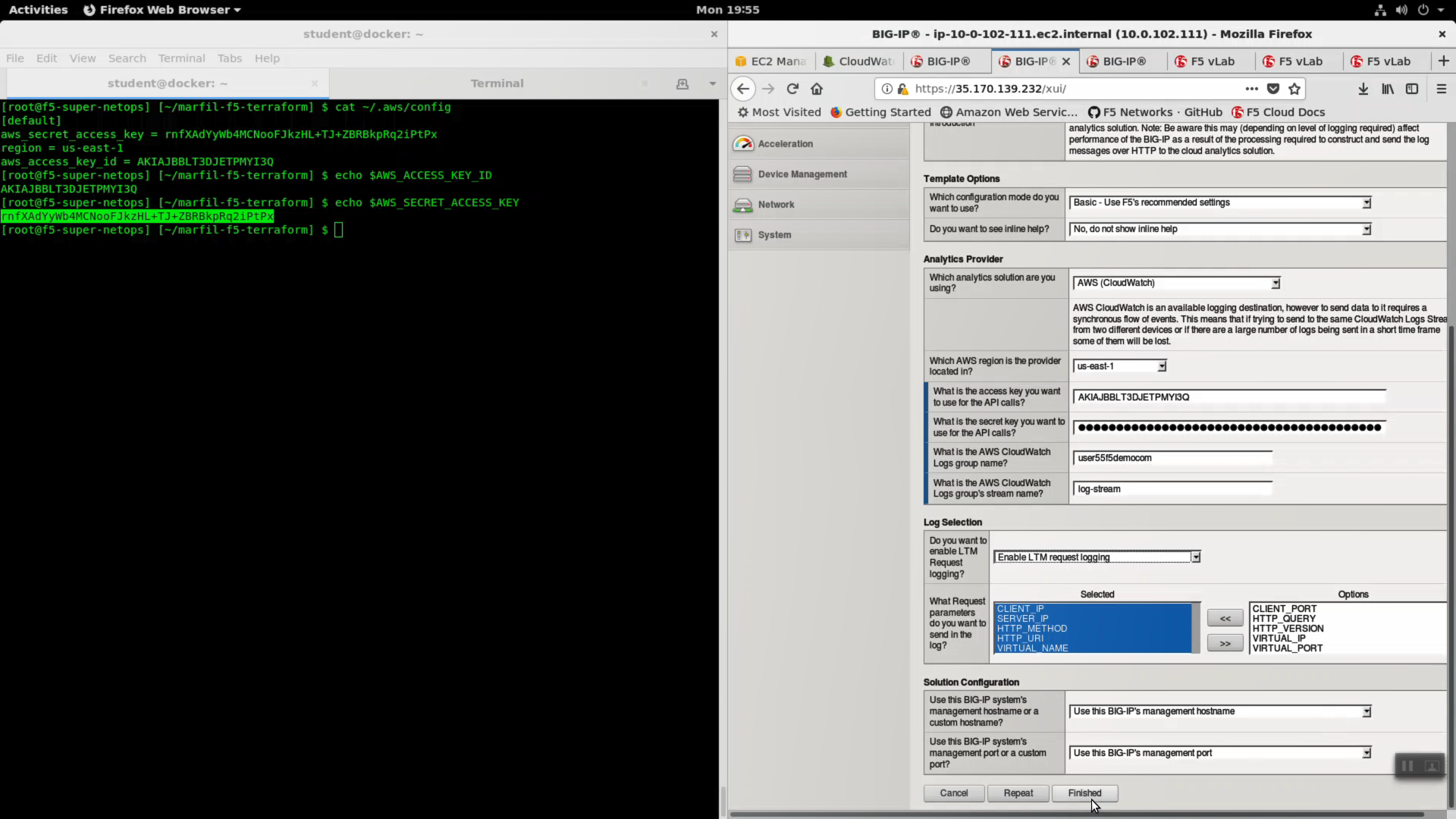
Create a new cloud_logger iApp. HTTPS to the Configuration Utility (Web UI) of Big-IP1 (assuming that is the ACTIVE device and not STANDBY).
iApps => Application Services => Name: cloudwatch. Template: f5.cloud_logger.v1.0.0. Click [Finished].
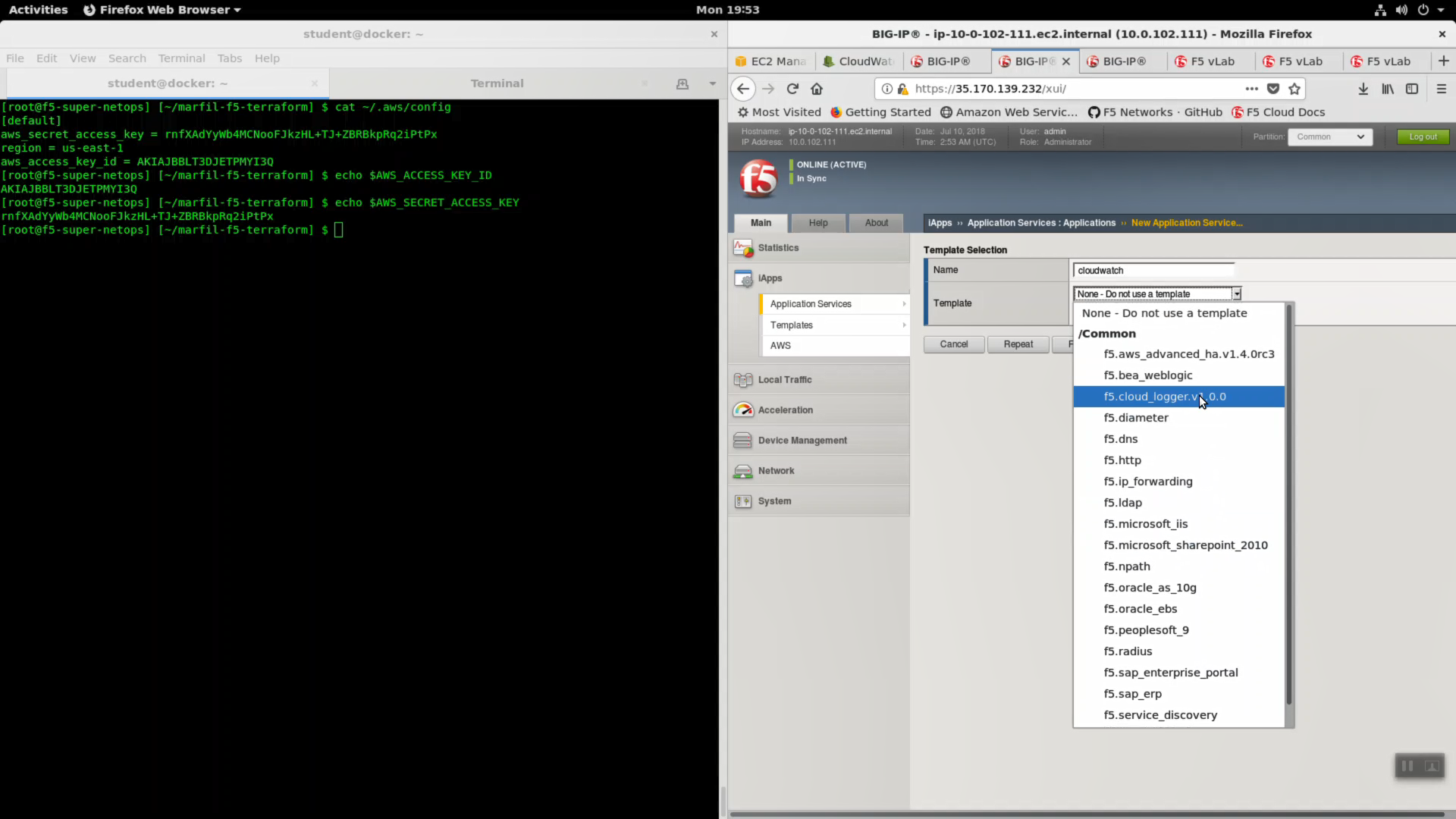
| Question | value |
|---|---|
| Name | cloudwatch |
| Template | f5.cloud_logger.v1.0.0 |
| Which AWS region is the provider located in? | us-east-1 |
| What is the access key you want to use for the API calls? | value of $AWS_ACCESS_KEY_ID |
| What is the secret key you want to use for the API calls? | value of $AWS_SECRET_ACCESS_KEY |
| What is the AWS CloudWatch Logs group name? | log group name i.e. user55labcom |
| What is the AWS CloudWatch Logs group’s stream name? | log-stream |
| Do you want to enable LTM Request logging? | Enable LTM request logging |
Click [Finished].
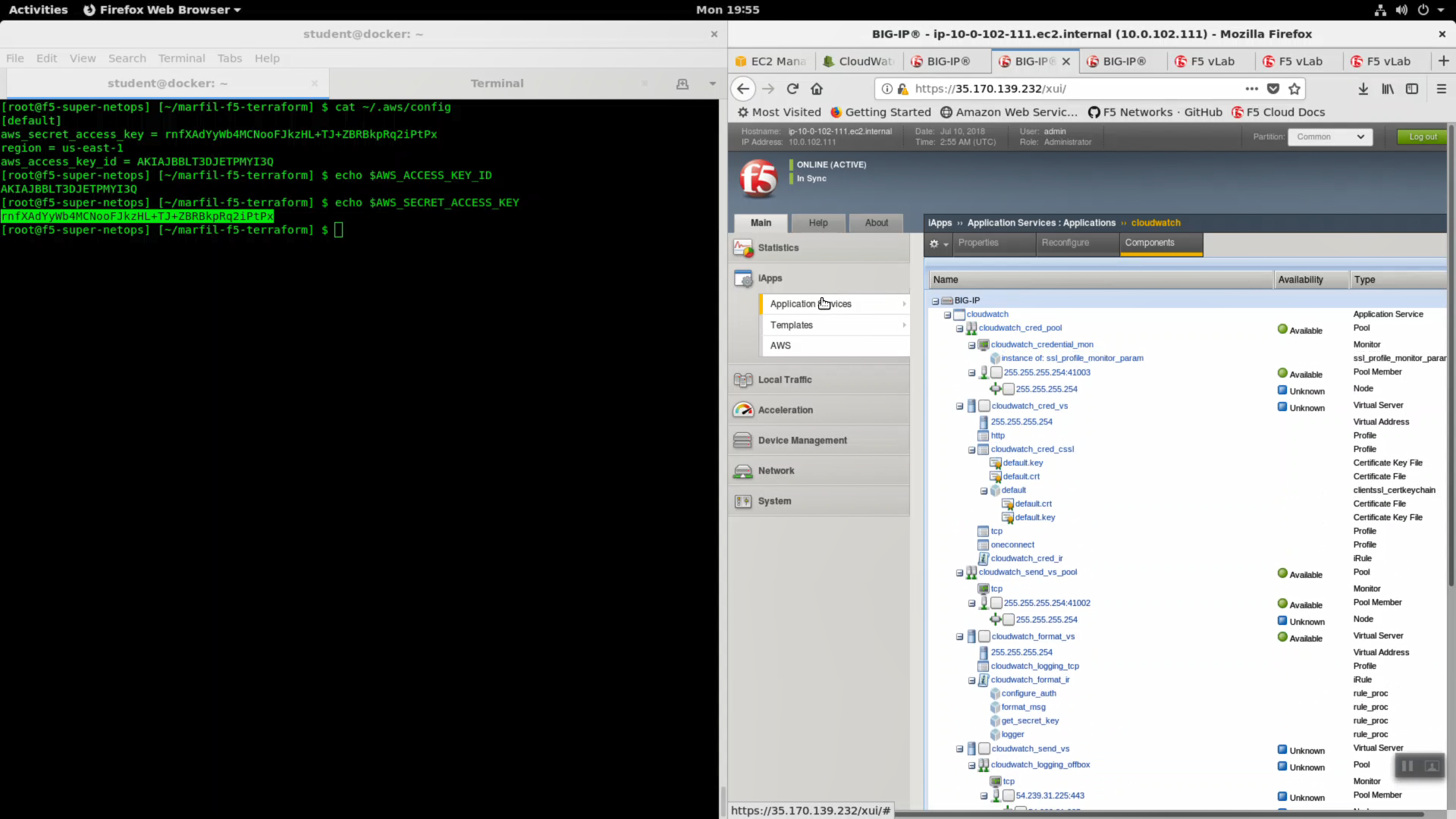
The logging components have been created!
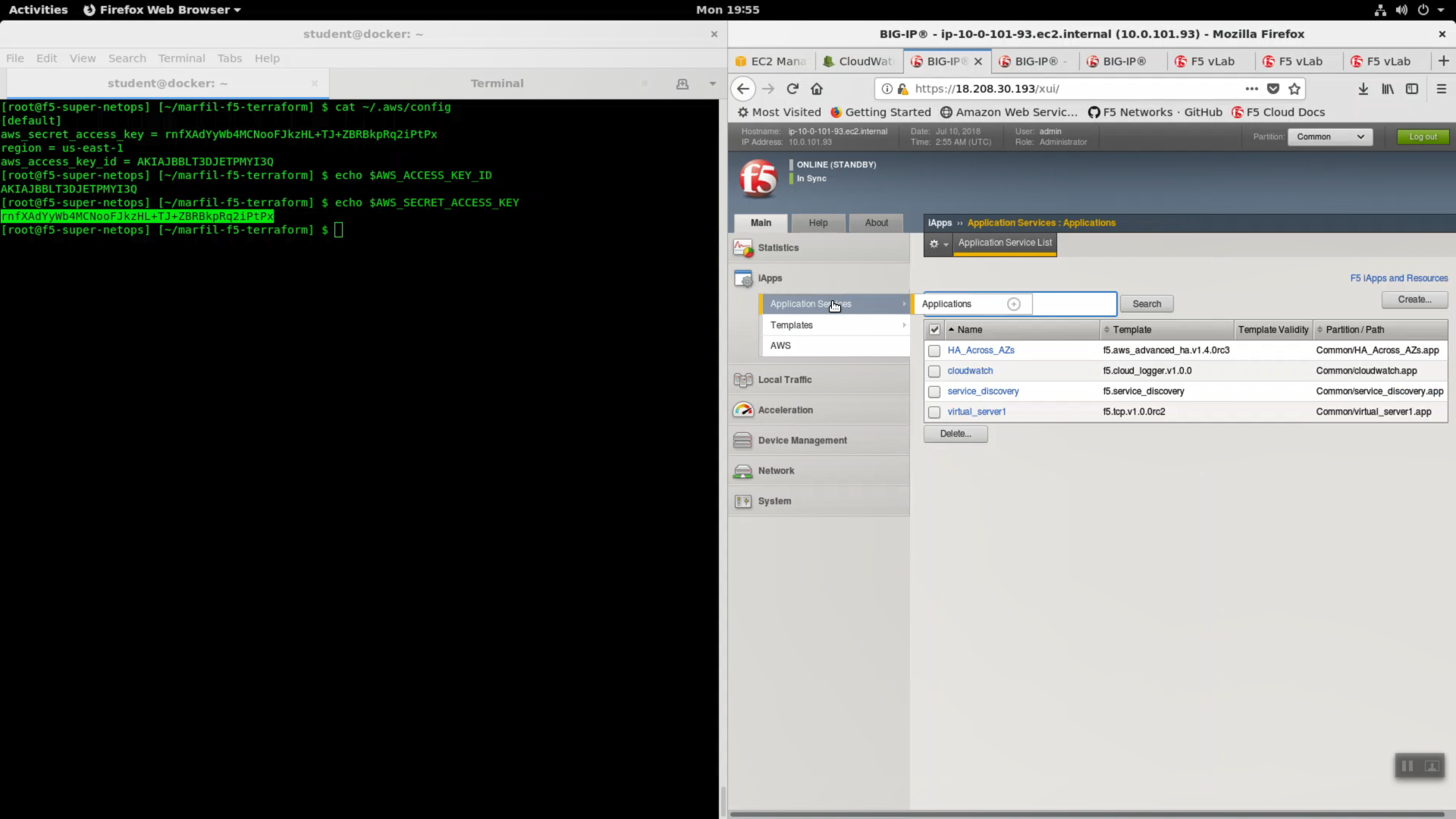
HTTPS to the Configuration Utility (Web UI) of Big-IP2 (if that is the standby). Look in the upper left-hand corner. Confirm you are on the STANDBY. All of the iApp changes are kept in sync between active and standby devices.
HTTPS to the Configuration Utility (Web UI) of Big-IP1 (assuming that is the ACTIVE device and not STANDBY).
iApps => Application Services => virtual_server1.
Attention
Before completing the next few steps, DISABLE STRICT UPDATES for the f5.tcp.v1.0.0rc2 iApp named virtual_server1 in our example.
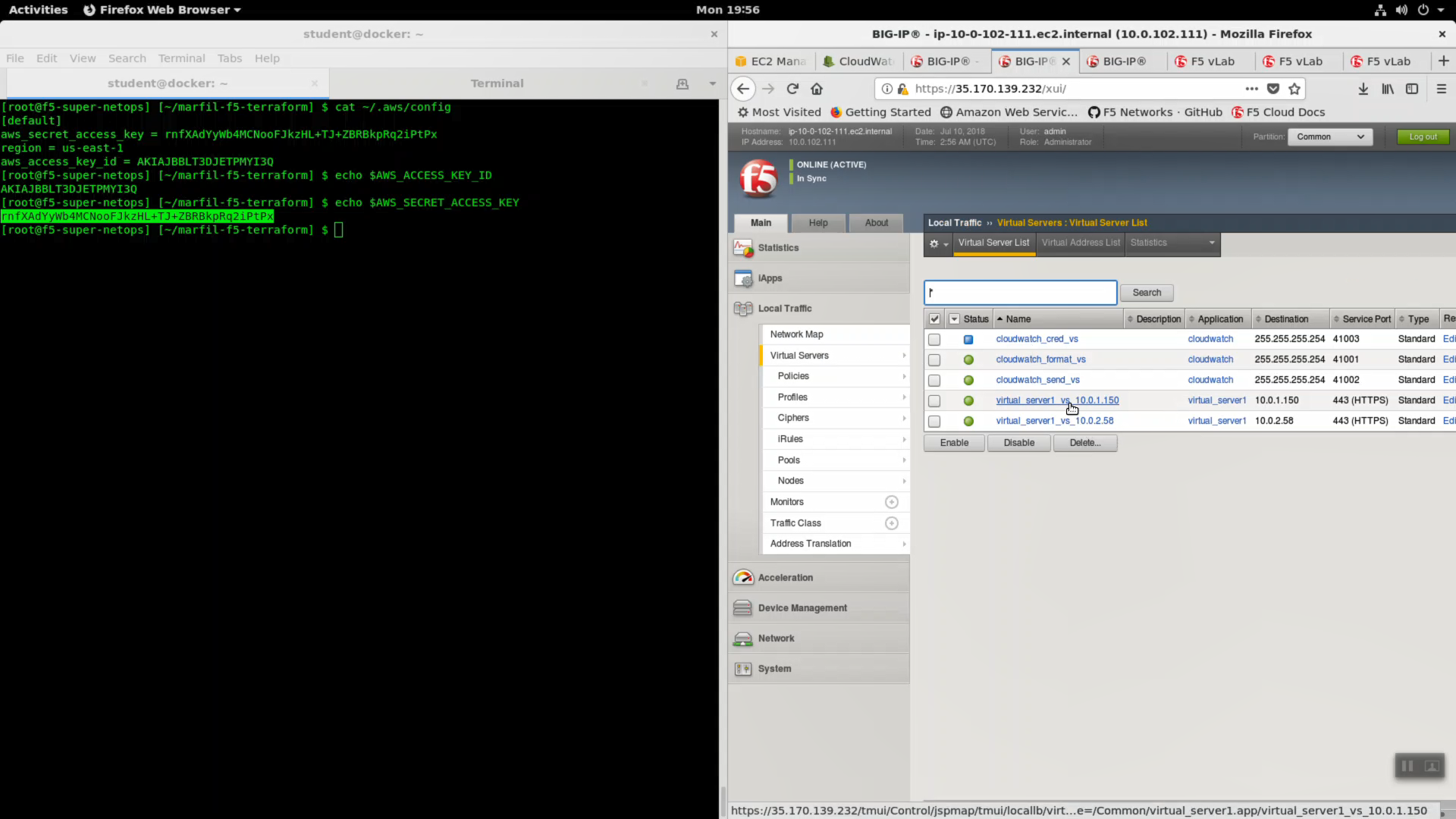
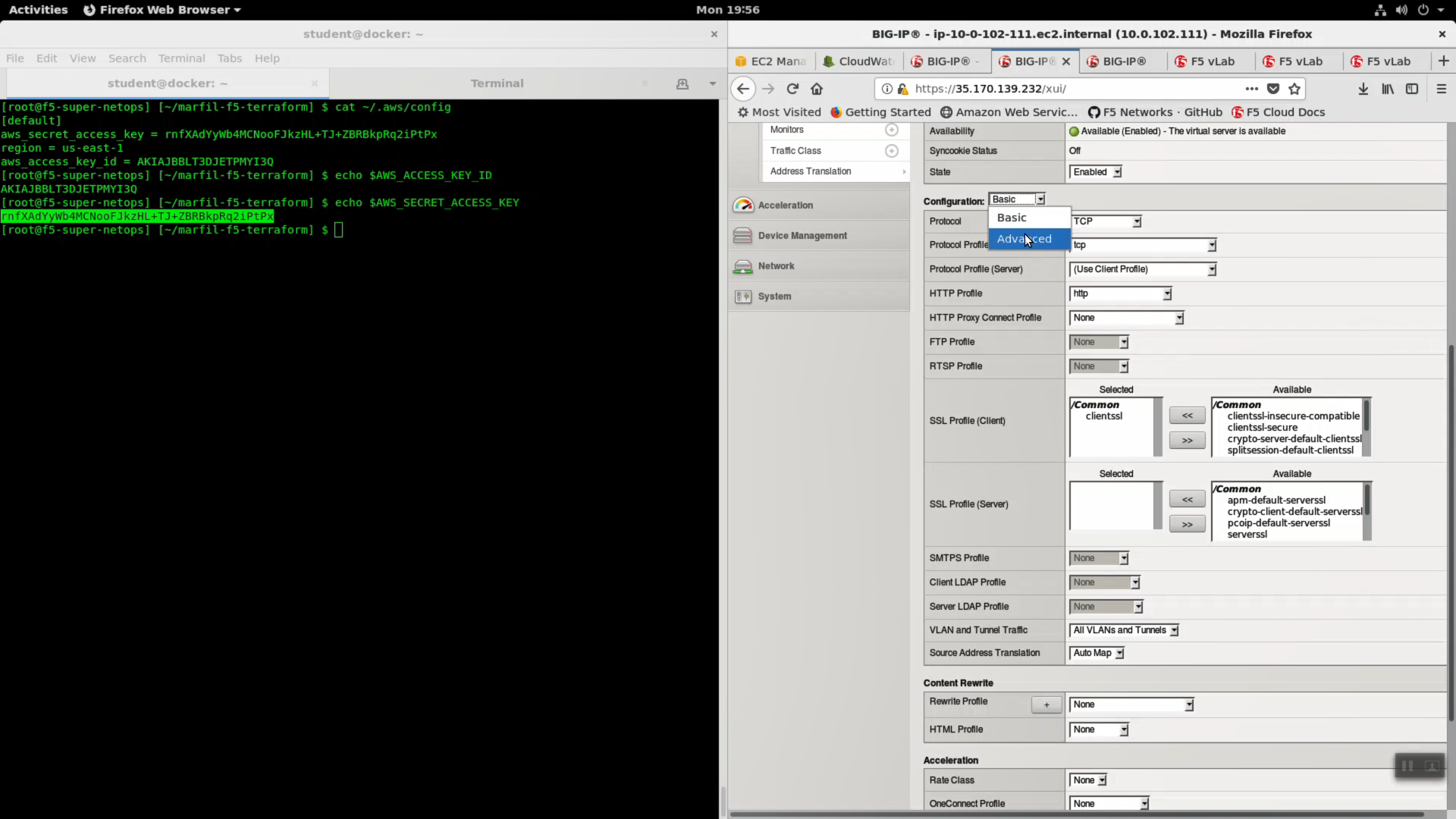
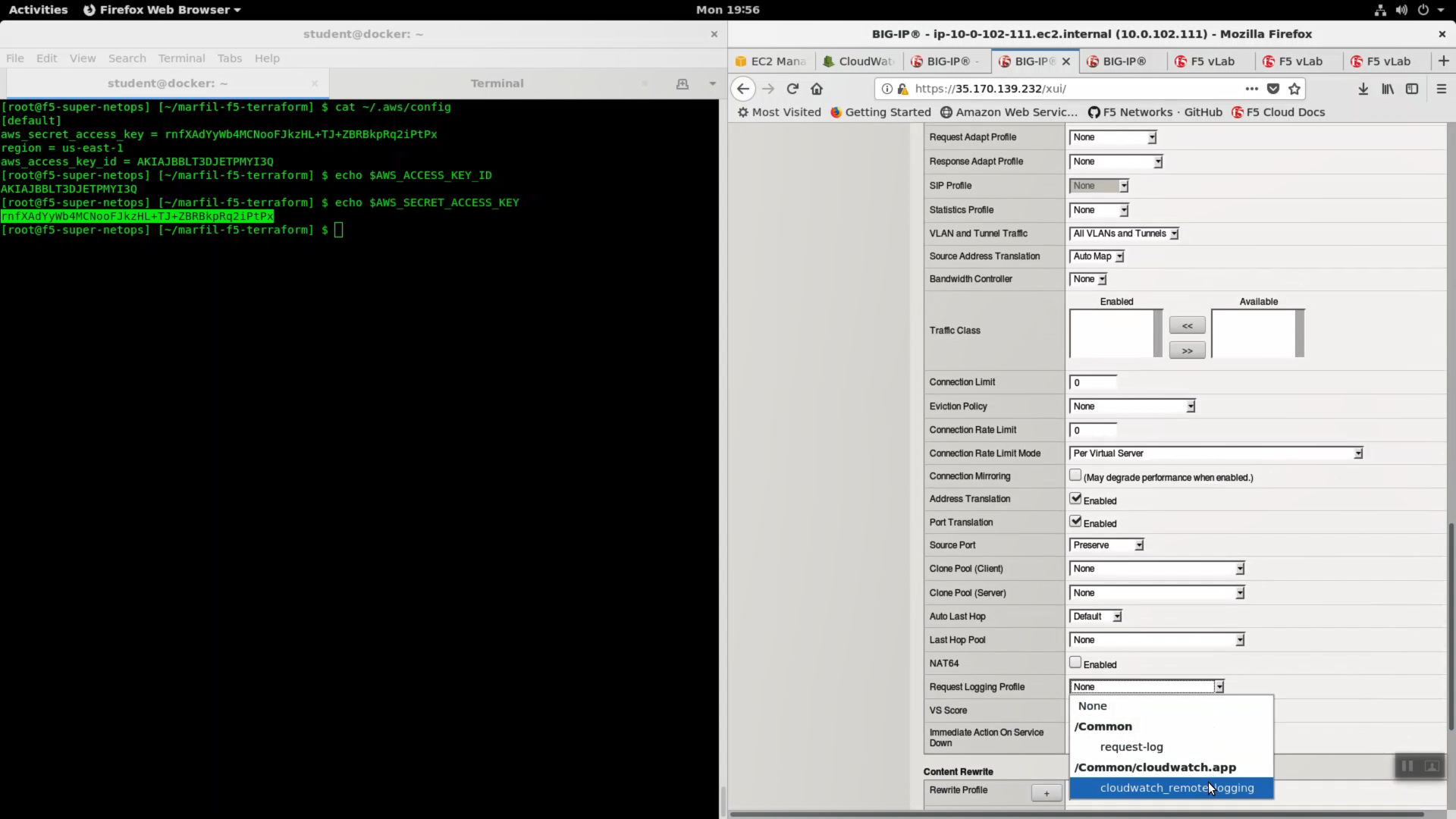
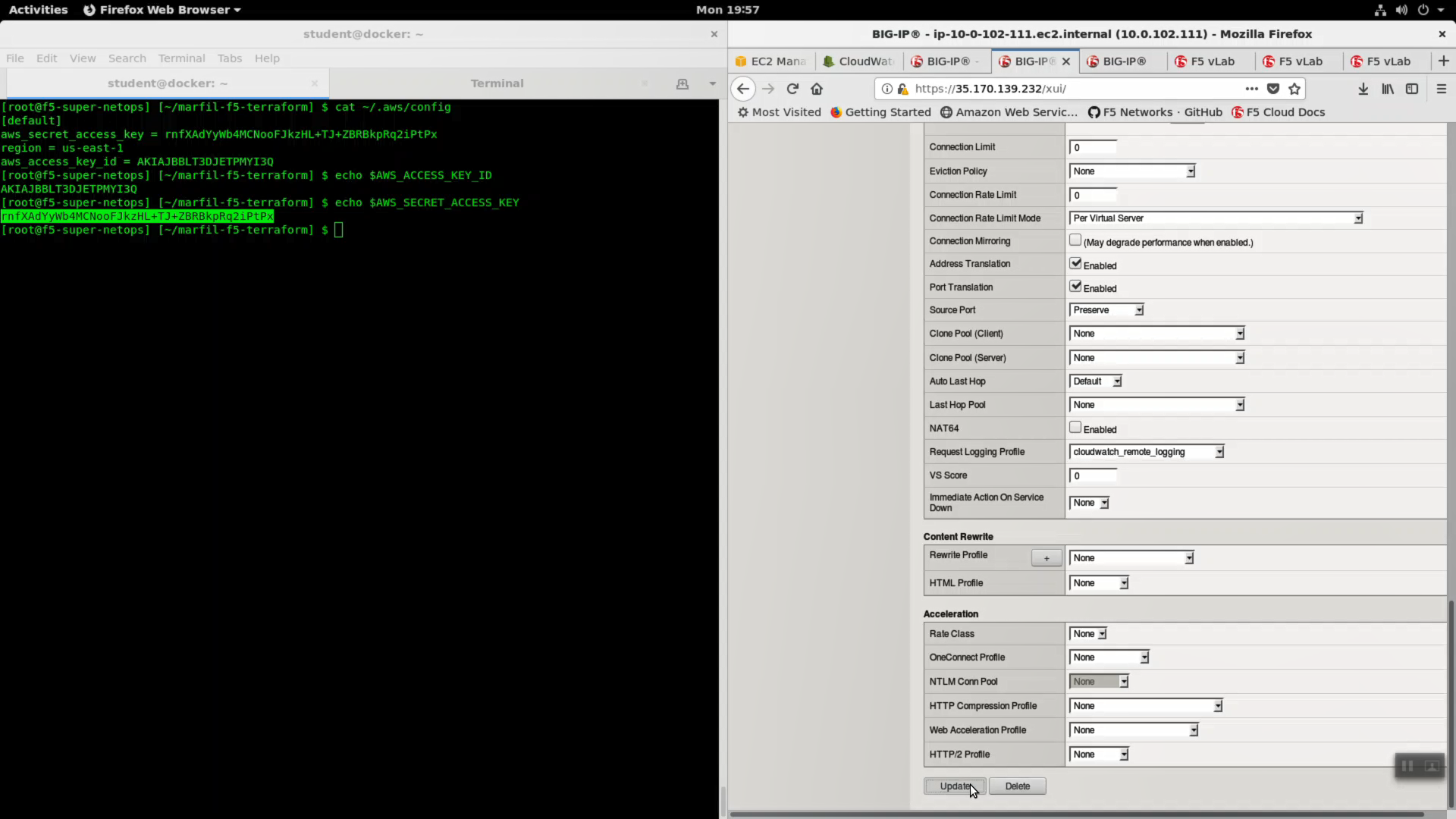
Local Traffic => Virtual Servers => virtual_server1_vs.10.0.1.x.
- Choose “Advanced” from the dropdown.
- Select SSL Profile(Client): clientssl
- Change HTTP Profile to “http”
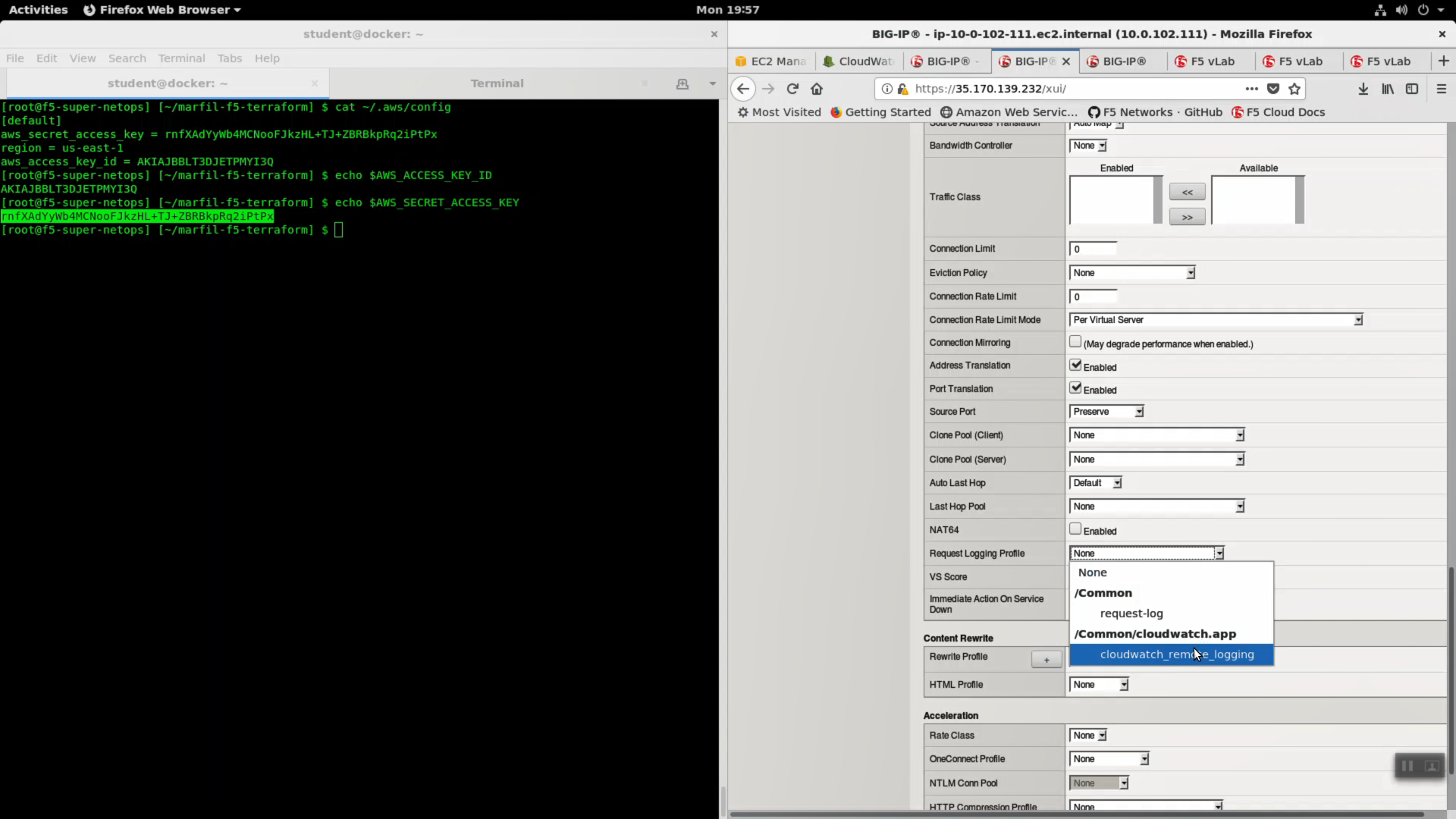
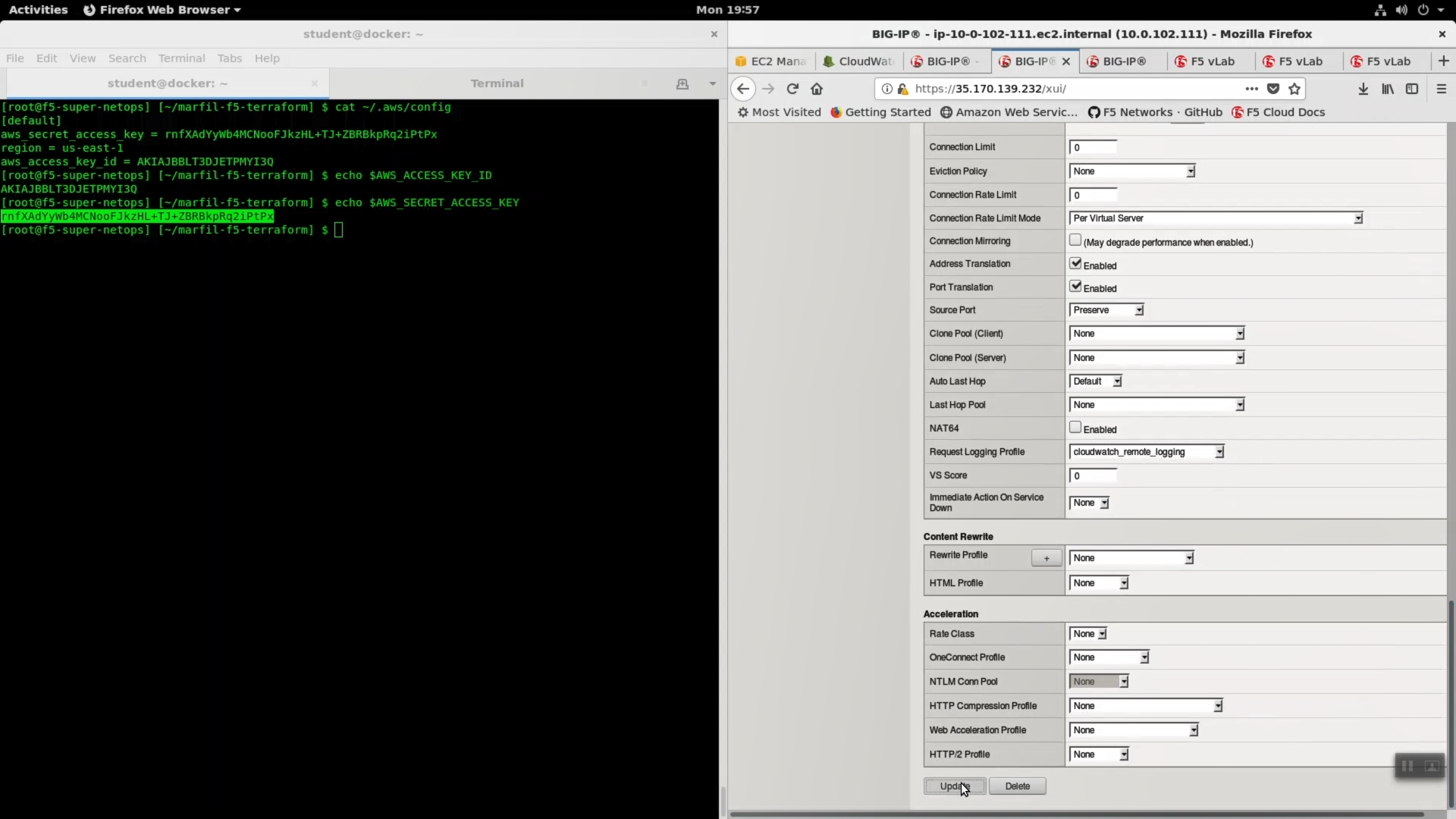
- Request Logging Profile: cloudwatch_remote_logging
Click [Update].
Do the same for the second virtual server. Local Traffic => Virtual Servers => virtual_server1_vs.10.0.1.x.
- Choose “Advanced” from the dropdown.
- Select SSL Profile(Client): clientssl
- Change HTTP Profile to “http”
- Request Logging Profile: cloudwatch_remote_logging
Click [Update].
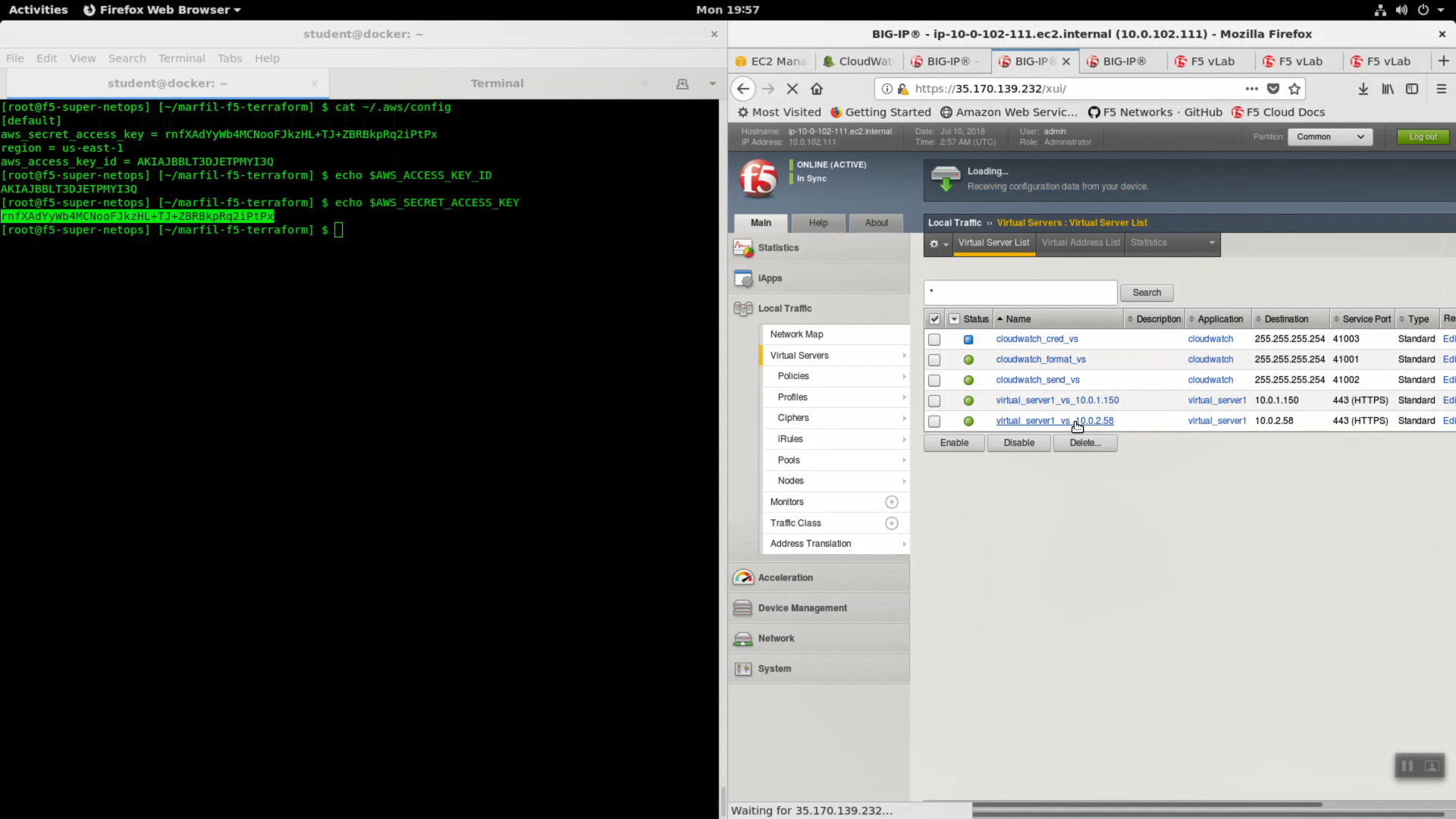
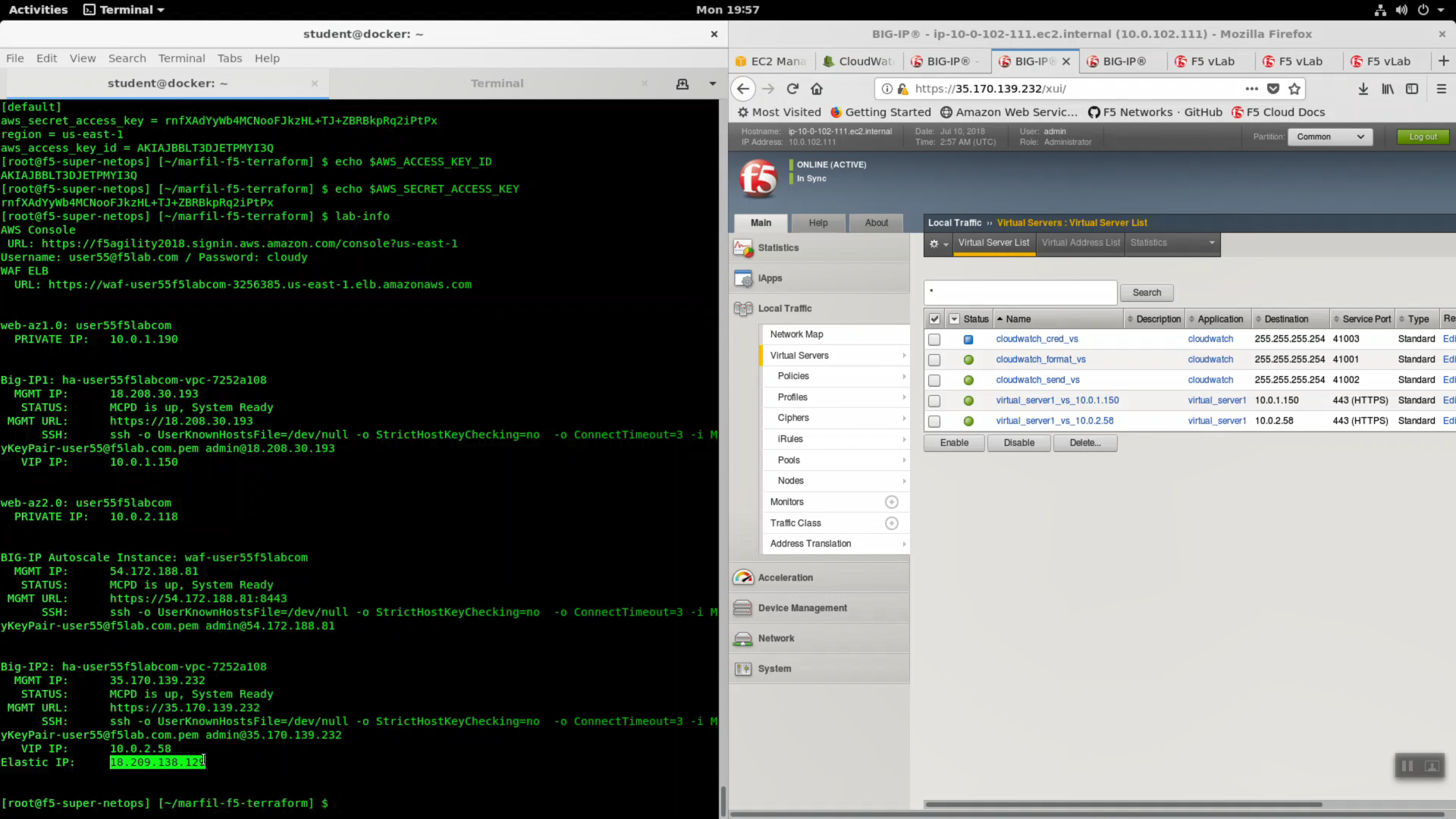
Run the lab-info command. Note the Elastic IP.
lab-info
HTTPS to the Elastic IP to test request logging. Refresh with [F5] key for 15 seconds to generate a modest amount of traffic.
Attention
Some lab testers reported an incompatibility issue with Mozilla Firefox on Linux and the AWS CloudWatch console. If Firefox doesn’t render the CloudWatch console, switch to Google Chrome for this part of the lab.
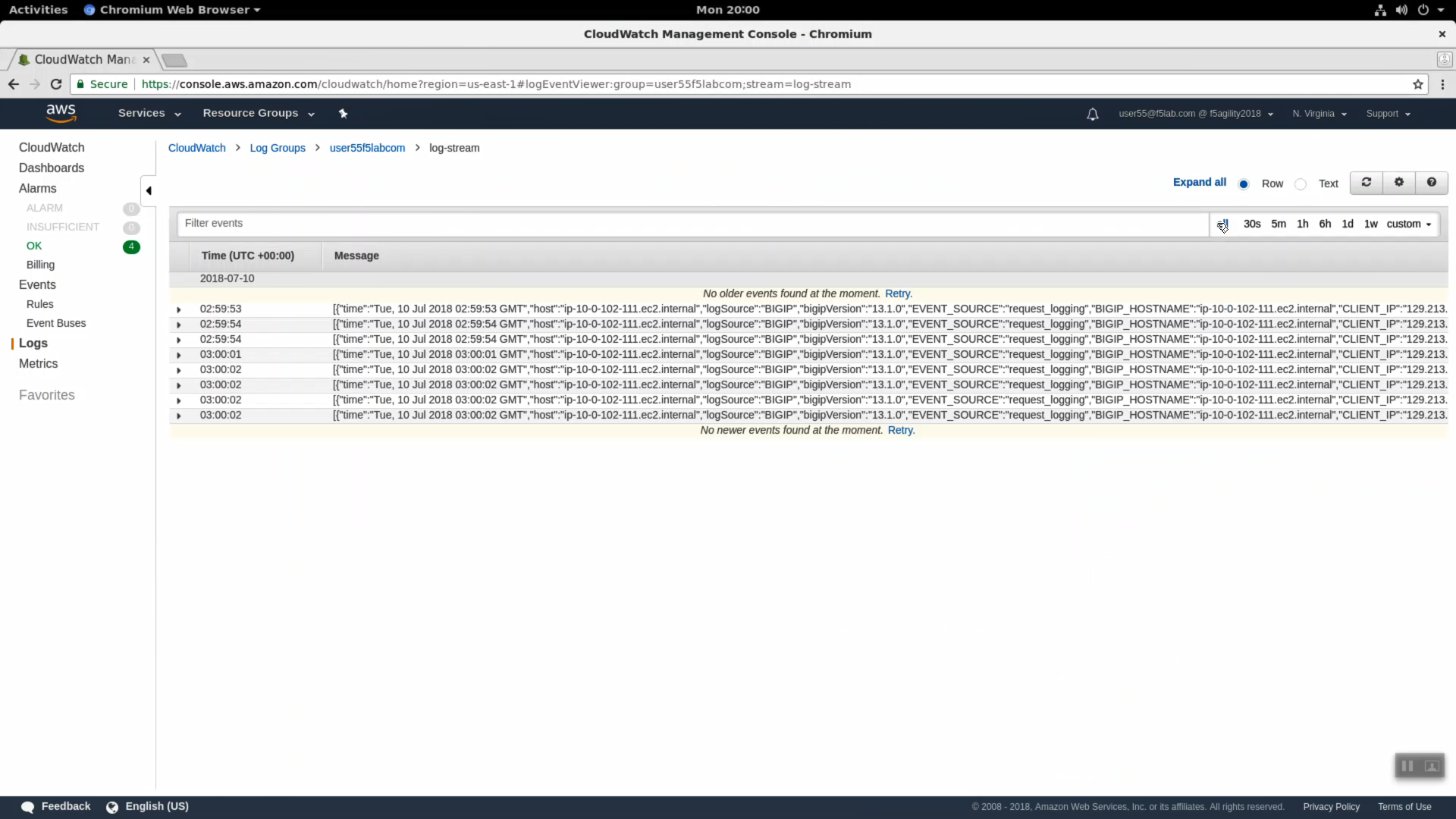
From the AWS Console, Services => Management Tools => CloudWatch => Log Groups. Select your log group and log-stream.
You will see the http request logs.
Expand a log entry to see more detail.
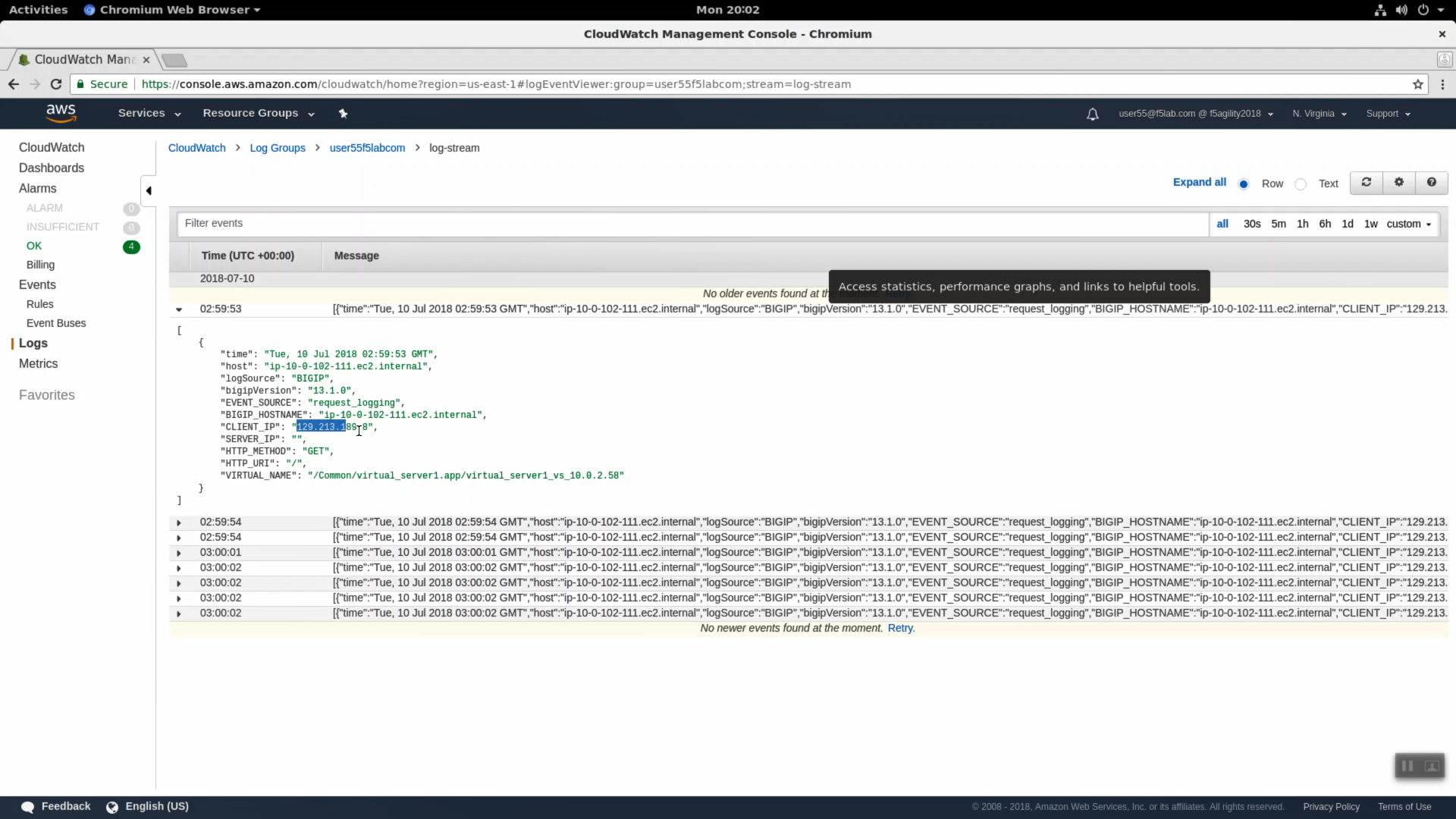
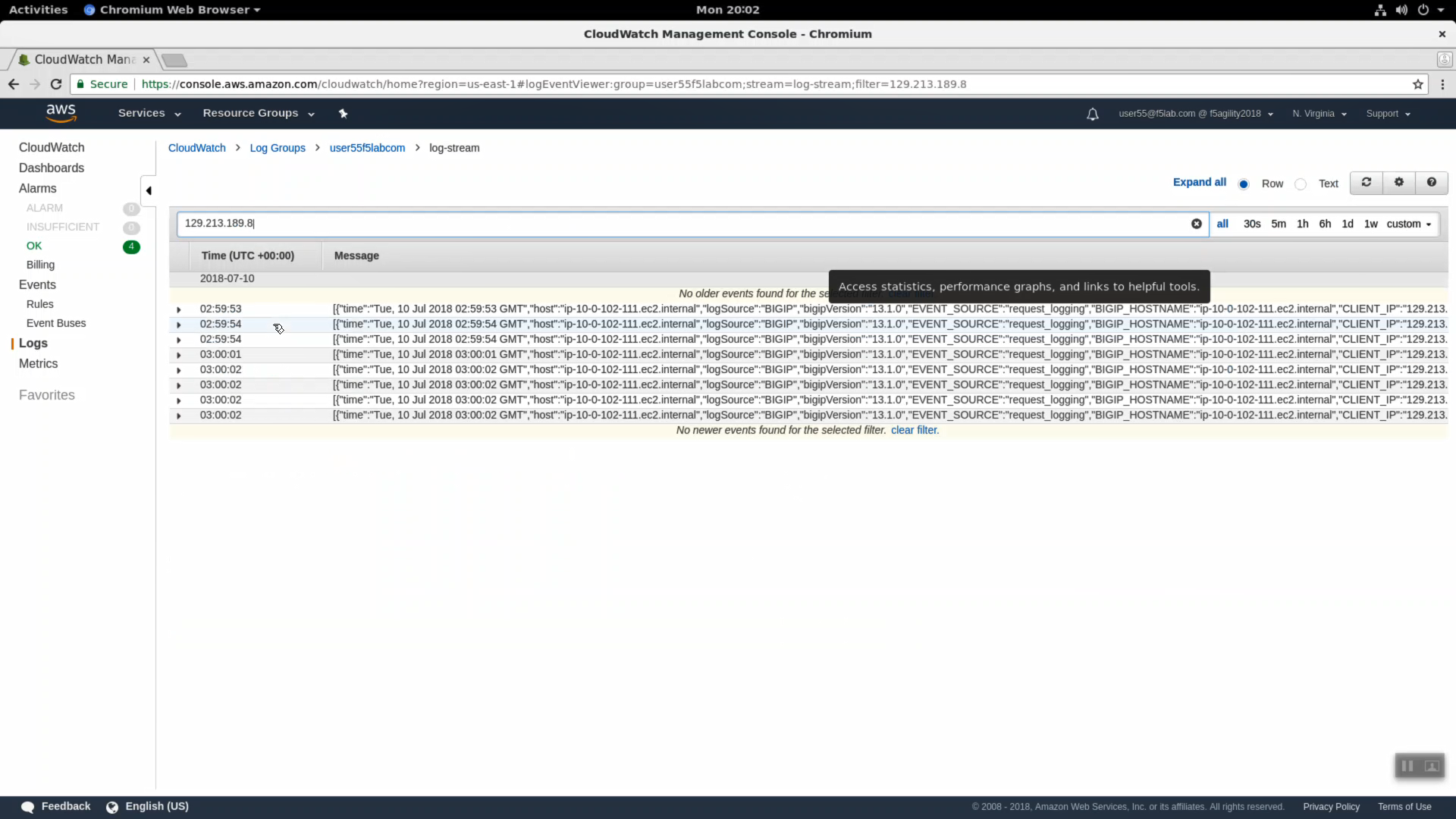
Copy the CLIENT_IP of a request and use this CLIENT_IP in the “Filter events” search filter. In production you would filter search results by attributes such as CLIENT-IP to home in on relevant logs.